
Expert Verified, Online, Free.

SIMULATION -
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS -
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
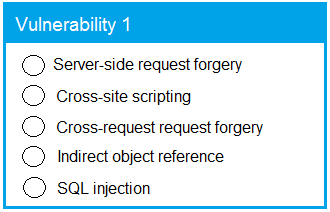
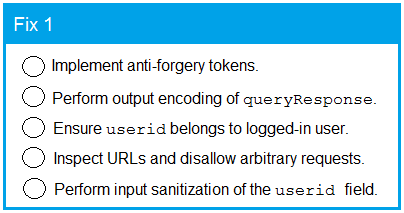
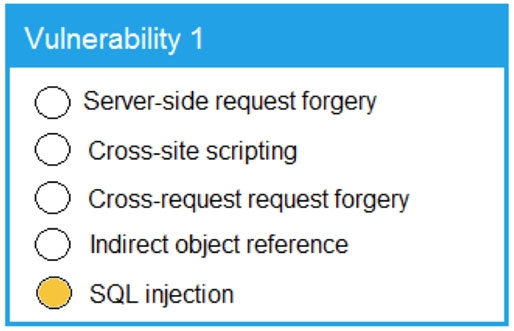
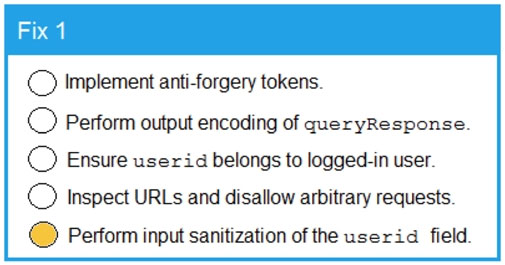
Code Snippet 1 -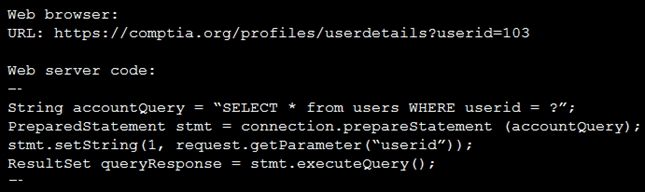
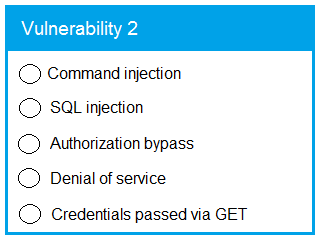
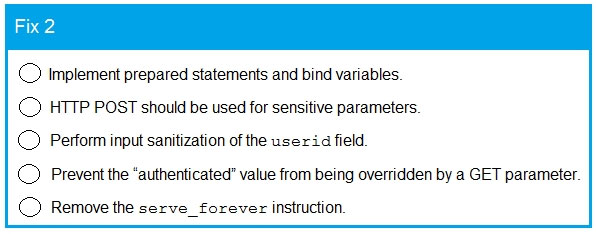
Code Snippet 2 -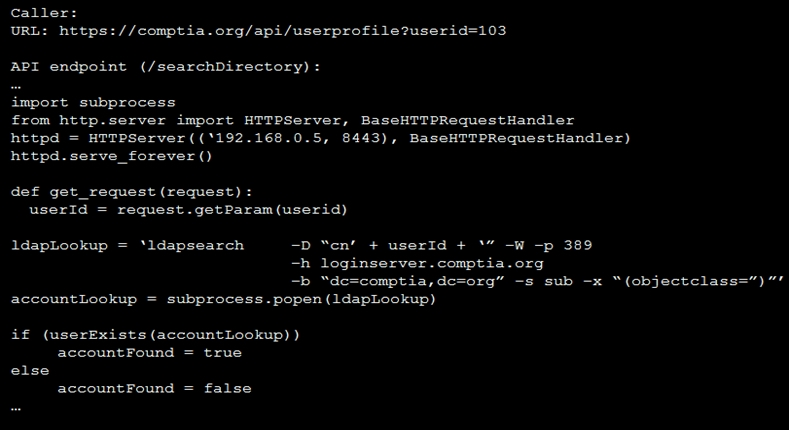
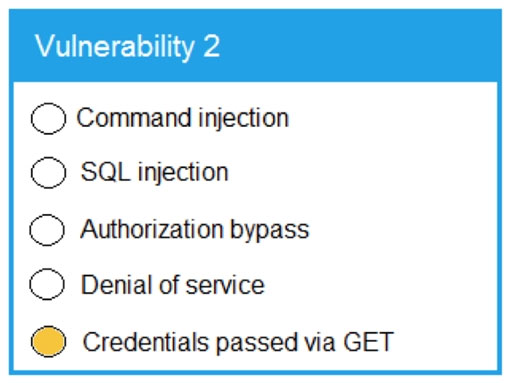
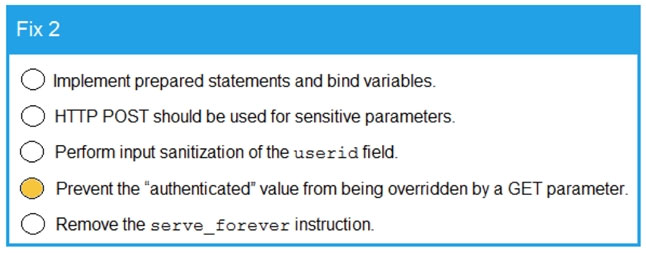
quagga
2 years, 4 months agoDrDoMe
2 years, 4 months agoquagga
2 years, 3 months agoAaronS1990
10 months agotefyayaydu
5 months, 2 weeks agoarawaco
2 years, 6 months agoarawaco
2 years, 6 months ago