

A company's Security Engineer is copying all application logs to centralized Amazon S3 buckets. Currently, each of the company's application is in its own AWS account, and logs are pushed into S3 buckets associated with each account. The Engineer will deploy an AWS Lambda function into each account that copies the relevant log files to the centralized S3 bucket.
The Security Engineer is unable to access the log files in the centralized S3 bucket. The Engineer's IAM user policy from the centralized account looks like this: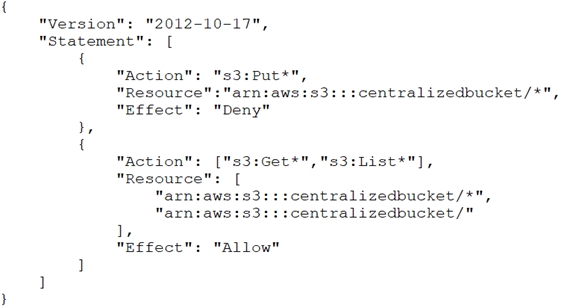
The centralized S3 bucket policy looks like this: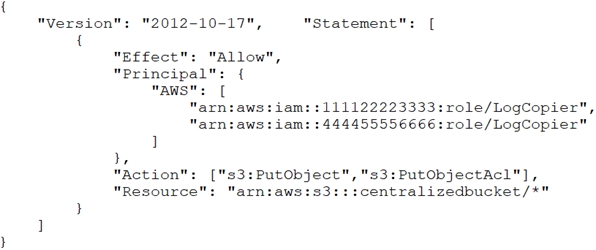
Why is the Security Engineer unable to access the log files?
trongod05
Highly Voted 3 years agoRaphaello
Most Recent 1 year, 4 months agoRaphaello
1 year, 4 months agoRaphaello
1 year, 4 months agoaddy_prepare
1 year, 10 months agoBlissfulCheetah
2 years agoTerrenceC
2 years, 6 months agosapien45
2 years, 10 months agotinyflame
3 years, 6 months agowahlbergusa
3 years, 8 months agonainakaexam
3 years, 8 months agonainakaexam
3 years, 8 months agonainakaexam
3 years, 8 months agoDerekKey
3 years, 8 months agorhinozD
3 years, 8 months agothuyeinaung
2 years, 8 months agothuyeinaung
2 years, 8 months agoHaz56
3 years, 8 months agoDaniel76
3 years, 8 months agosanjaym
3 years, 8 months agodisposable1989
3 years, 9 months agodisposable1989
3 years, 9 months ago