

A security engineer noticed an anomaly within a company EC2 instance as shown in the image. The engineer must now investigate what is causing the anomaly.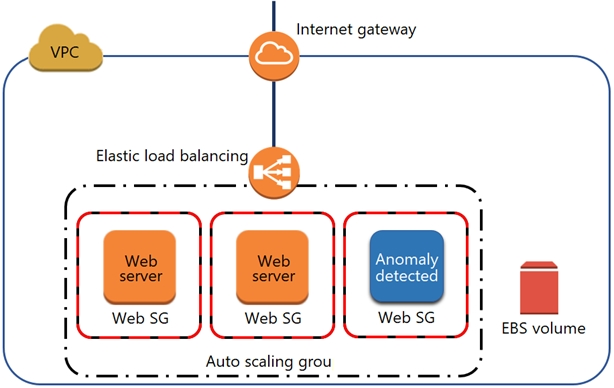
What are the MOST effective steps to take to ensure that the instance is not further manipulated, while allowing the engineer to understand what happened?
DayQuil
Highly Voted 3 years, 8 months agoRaphaello
Most Recent 1 year, 4 months agoGreen53
2 years agosamCarson
2 years agopal40sg
2 years, 1 month agojawiem
2 years, 2 months agoITGURU51
2 years, 2 months agoCyp
2 years, 3 months agoawsguru1998
2 years, 4 months agoAzureDP900
2 years, 4 months agoBalki
2 years, 11 months agotrongod05
3 years agosapien45
2 years, 11 months agoDmosh
2 years, 2 months agoRadhaghosh
3 years, 5 months agokiev
3 years, 8 months agokhchan123
3 years, 8 months agorefuz
3 years, 8 months agocldy
3 years, 8 months ago