

After a recent security audit involving Amazon S3, a company has asked for assistance reviewing its S3 buckets to determine whether the data is properly secured. The first S3 bucket on the list has the following bucket policy: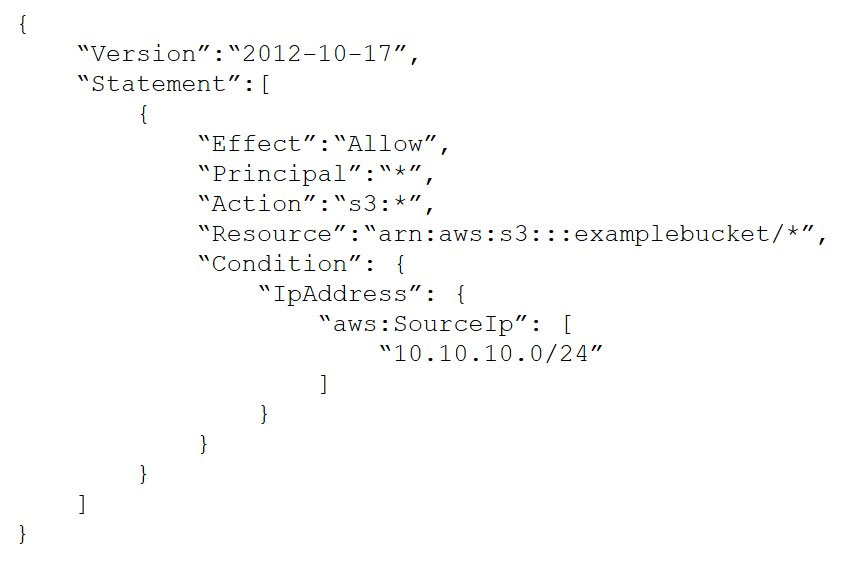
In this bucket policy sufficient to ensure that the data is not publicly accessible?
hk436
Highly Voted 3 years, 8 months agoMassoom
3 years, 1 month ago1awssec
Highly Voted 3 years, 8 months agoyorkicurke
Most Recent 1 year, 6 months agoyorkicurke
1 year, 6 months agosapien45
2 years, 12 months agoTigerInTheCloud
3 years, 3 months agorootblack
3 years, 3 months agoMassoom
3 years agoDingjieDanielYang
3 years, 4 months agobull2
3 years, 5 months agoLaLune
3 years, 5 months agoNSF2
3 years, 5 months agocloudchica
3 years, 6 months agosam_live
3 years, 6 months agoargol
3 years, 7 months agojtzt2003
3 years, 8 months agodfranco76
3 years, 8 months agodfranco76
3 years, 8 months agoJohn129087
3 years, 8 months agoCloudMasterGuru
3 years, 8 months agoGabeDevOps
3 years, 8 months agodumma
3 years, 9 months ago