

A recent security audit identified that a company's application team injects database credentials into the environment variables of an AWS Fargate task. The company's security policy mandates that all sensitive data be encrypted at rest and in transit.
Which combination of actions should the security team take to make the application compliant with the security policy? (Choose three.)
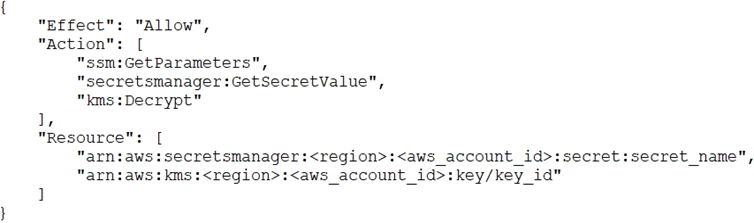
Raphaello
1 year, 4 months agopupsik
1 year, 8 months agoaddy_prepare
1 year, 11 months agopal40sg
2 years, 1 month agoDmosh
2 years, 2 months agoITGURU51
2 years, 2 months agoMeizhen
2 years, 6 months agosapien45
2 years, 10 months agodmmbr
2 years, 10 months agovbal
2 years, 10 months agovbal
2 years, 10 months ago