

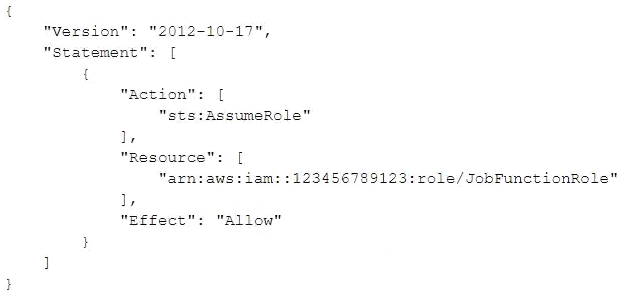
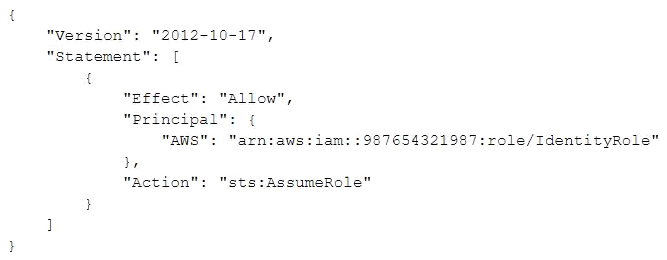
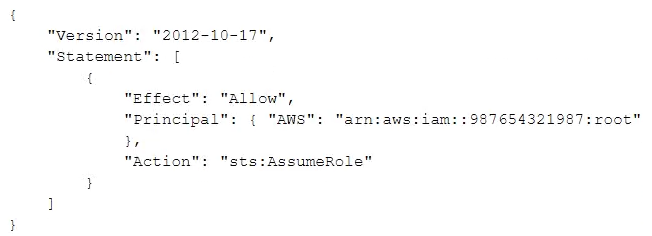
A company uses identity federation to authenticate users into an identity account (987654321987) where the users assume an IAM role named IdentityRole. The users then assume an IAM role named JobFunctionRole in the target AWS account (123456789123) to perform their job functions.
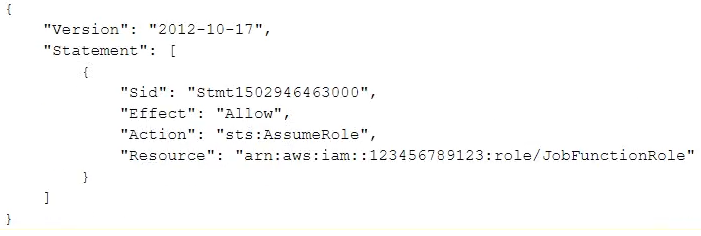
A user is unable to assume the IAM role in the target account. The policy attached to the role in the identity account is: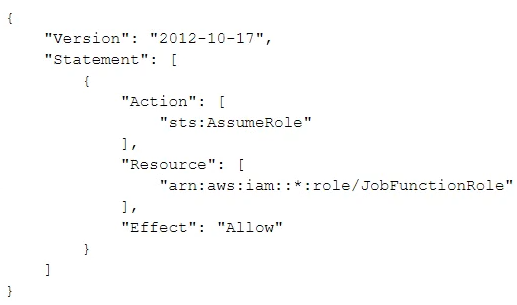
What should be done to enable the user to assume the appropriate role in the target account?
sapien45
Highly Voted 2 years, 10 months agoStepFunckyTown
2 years, 9 months agoHieuTT
2 years, 8 months agoITGURU51
2 years, 1 month agoRaphaello
Most Recent 1 year, 4 months agocaptainpike
1 year, 12 months agocaptainpike
1 year, 12 months agoBillD_1235
2 years agoITGURU51
2 years, 1 month agomichele_scar
2 years, 1 month agopeddyua
2 years, 4 months agojishrajesh
2 years, 6 months agoawsmonkey
2 years, 6 months agojAWStest
2 years, 7 months agoJeongPock2y
2 years, 8 months agoQasimac
2 years, 8 months agoyyy
2 years, 8 months agoBKV83
2 years, 9 months agoashmek
2 years, 9 months ago