

A company is running third-party WAF software on AWS. The company's security team discovers that the third-party WAF software has vulnerabilities that can lead to server-side request forgery (SSRF) attacks. Because of this discovery, the security team mandates that the entire AWS infrastructure must use version 2 of the instance metadata service (IMDSv2).
At the planned completion of the implementation of IMDSv2, the security team uses the Amazon CloudWatch metric Amazon EC2:MetadataNoToken and determines that hundreds of old IMDSv1 requests still are occurring each day. The security team is willing to risk the availability of the company's application to finish this implementation.
Which combination of steps should the security team take to complete the migration to IMDSv2 in the AWS environment? (Choose two.)
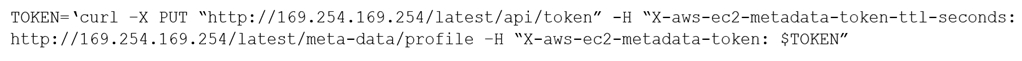
Toptip
2 years agoHieuTT
2 years, 8 months agosapien45
2 years, 10 months agomh777
2 years, 10 months ago