

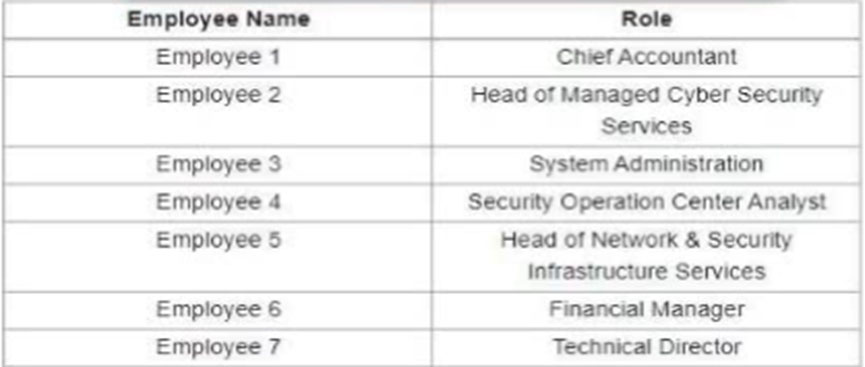
Refer to the exhibit. A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source. After the attacker produces many of failed login entries it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
Comments