

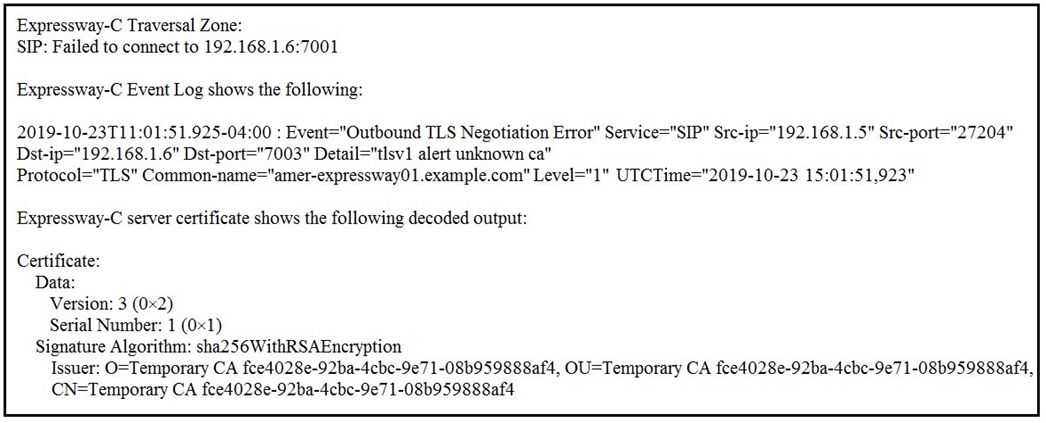
Refer to the exhibit. An Expressway-C and Expressway-E are configured for B2B calling and the Expressway-E zone is set to TLS Verify Currently, calls do not reach the Expressway-C. The Traversal Client zone on the Expressway-C for B2B reports the information in the exhibit for the Peer 1 address.
Which action resolves this error?
chamba87
Highly Voted 2 years, 9 months agoiamnoone
Most Recent 3 months, 1 week agoCollabinski
11 months agoCollabinski
11 months agoCollabinski
11 months, 1 week agojonycakes
1 year, 12 months agoOmitted
1 year, 6 months agokhader09
3 years, 2 months agoBangBang86
3 years, 4 months ago