

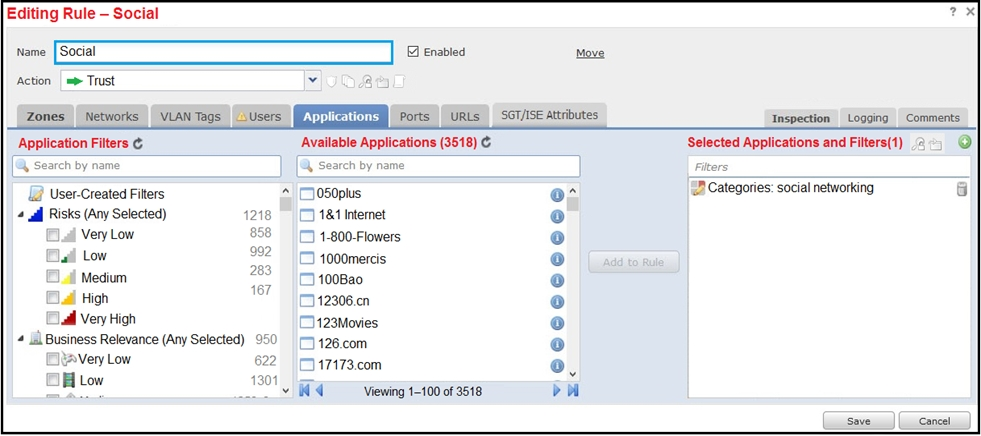
Refer to the exhibit. An organization has an access control rule with the intention of sending all social media traffic for inspection. After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed. What must be done to address this issue?
4study
Highly Voted 2 years, 2 months agomajid94
Highly Voted 2 years, 7 months agoDID123
Most Recent 12 months agoaaInman
1 year, 7 months agoxziomal9
1 year, 7 months agoReece_S
1 year, 8 months agoBorZol
1 year, 4 months agoliqucika
2 years agoSarbi
2 years, 4 months agoAS04
2 years, 6 months agoBobster02
2 years, 8 months agomichingon
2 years, 8 months agokakakayayaya
2 years, 8 months ago