

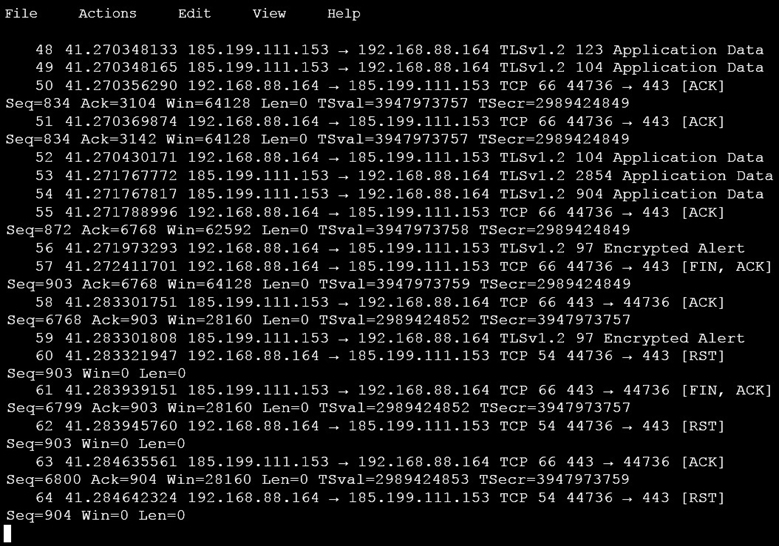
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
Which obfuscation technique is the attacker using?
mariodesa
Highly Voted 1 year, 6 months agoEng_ahmedyoussef
Most Recent 10 months agocy_analyst
10 months agoMevijil
1 year, 5 months agoseriously5000
1 year, 6 months agotor_nana
1 year, 7 months ago