

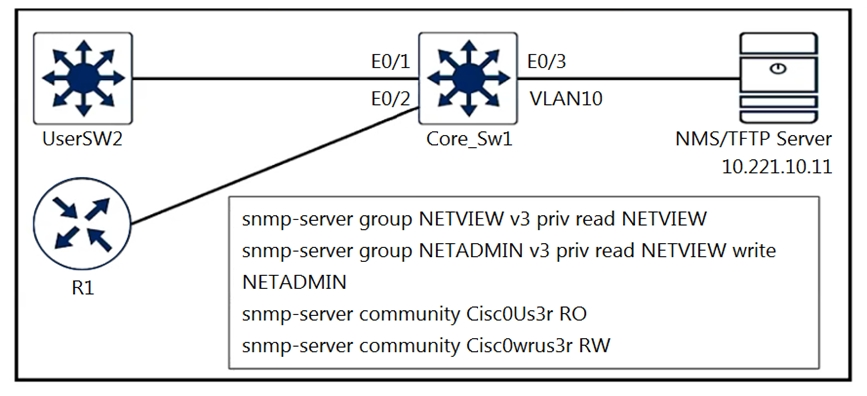
Refer to the exhibit. A junior engineer configured SNMP to network devices. Malicious users have uploaded different configurations to the network devices using
SNMP and TFTP servers.
Which configuration prevents changes from unauthorized NMS and TFTP servers?
mrnipsnips
Highly Voted 2 years, 8 months agoSlinky
2 years, 5 months agoledesir
1 year, 8 months agobuddhagaut
1 year, 5 months agoMasterMatt
Highly Voted 2 years, 3 months agoRickAO76
Most Recent 1 year, 3 months agoZamanR
1 year, 7 months agoJey117
1 year, 9 months agoColmenarez
1 year, 11 months agoJOKERR
3 years, 2 months agoBolt_Action_Studios
3 years, 2 months ago