

Refer to the exhibit. A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end- user community?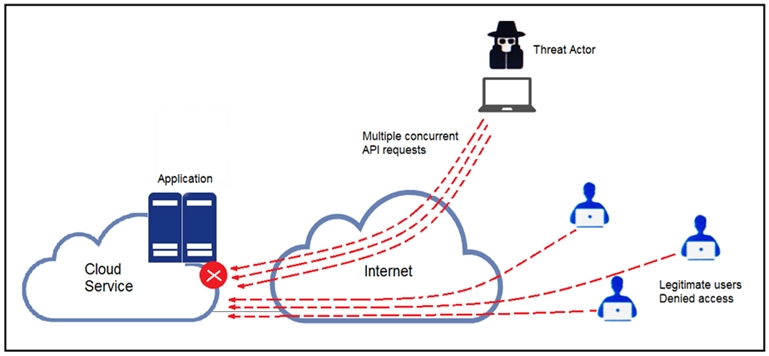
MoII
6 months, 1 week agoDeco123
1 year, 7 months agoEphert
1 year, 4 months agoRAVPN
1 year, 2 months agoVINTHAN
1 year, 8 months agoTOLU1985
2 years, 8 months ago