

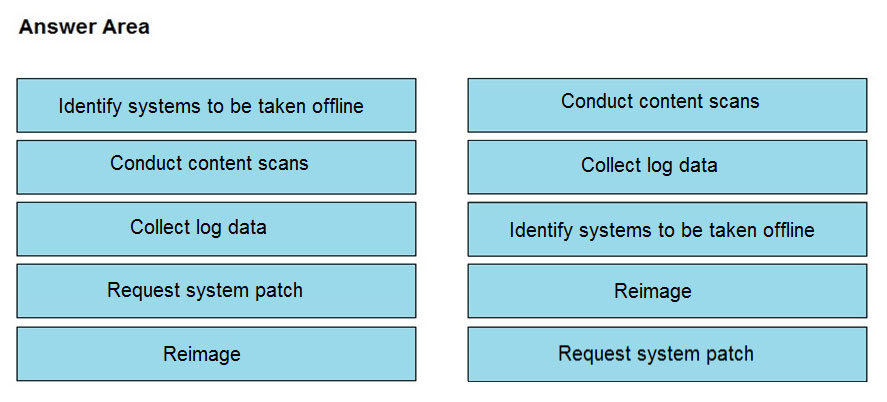
DRAG DROP -
An engineer notices that unauthorized software was installed on the network and discovers that it was installed by a dormant user account. The engineer suspects an escalation of privilege attack and responds to the incident. Drag and drop the activities from the left into the order for the response on the right.
Select and Place: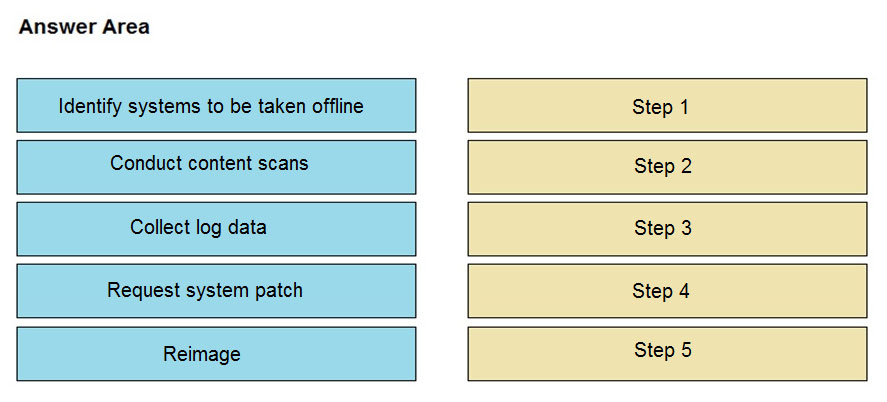
Geoaws
1 year, 2 months agoVic25H
12 months agoDrVoIP
1 year, 4 months agojaciro11
1 year, 1 month agojay_c_an
1 year, 1 month ago