

After reviewing the following packet, a cybersecurity analyst has discovered an unauthorized service is running on a company's computer.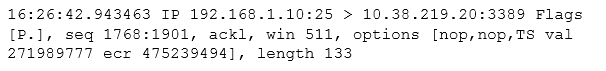
Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not impact other services?
s3curity1
Highly Voted 5 years, 2 months agoChiaretta
Most Recent 3 years, 6 months agoAcrisius
4 years, 7 months ago