

The Chief Information Security Officer (CISO) has asked the security analyst to examine abnormally high processor utilization on a key server. The output below is from the company's research and development (R&D) server.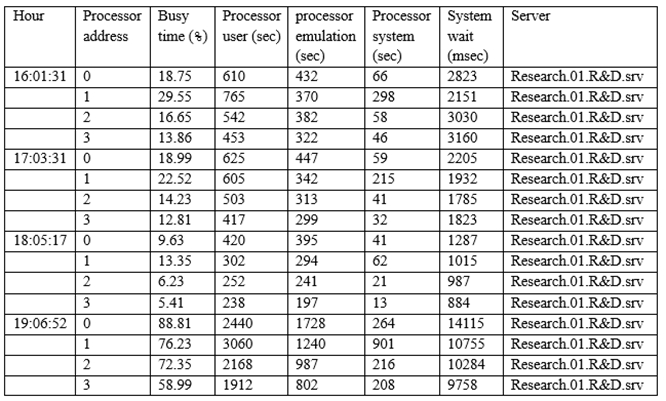
Which of the following actions should the security analyst take FIRST?
s3curity1
Highly Voted 5 years agos3curity1
5 years agoBigBo01010
Highly Voted 4 years, 11 months agoshakevia463
3 years, 6 months agowajdi
Most Recent 6 months, 3 weeks agosomsom
4 years, 3 months agopc_addict
4 years, 7 months agoAshfaq2
4 years, 8 months agoDeath2QuestionWriters
4 years, 8 months agoToyeeb
4 years, 10 months ago[Removed]
4 years, 9 months agoiphy
4 years, 11 months agoBlind_Hatred
5 years ago