

A security analyst has received reports of very slow, intermittent access to a public-facing corporate server. Suspecting the system may be compromised, the analyst runs the following commands: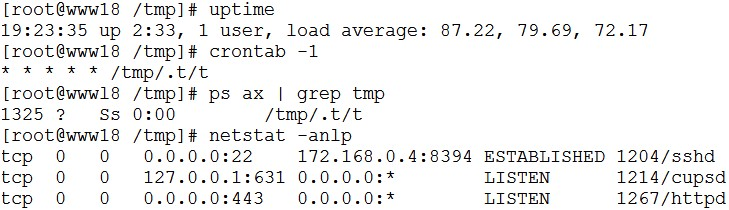
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Obi_Wan_Jacoby
Highly Voted 4 years, 3 months agoufovictim
4 years, 3 months agocomptia23
3 years, 8 months ago2Fish
2 years, 1 month agoI_heart_shuffle_girls
Highly Voted 4 years, 3 months agogrelaman
Most Recent 1 year, 8 months agogrelaman
1 year, 8 months agoXoomalla
1 year, 8 months agotatianna
2 years, 1 month agokhrid4
2 years, 1 month agoCatoFong
2 years, 2 months agoEric1234
2 years, 3 months agomiabe
2 years, 9 months agoJenG59
2 years, 11 months agoBlackdaRipper
3 years, 2 months agoHam_Solo
3 years, 9 months agoAlizadeh
4 years, 1 month agoAlizadeh
4 years, 1 month agoUmer24
4 years, 3 months agoBerlus
3 years, 11 months agoRokzyBalboa
4 years, 3 months agolollo1234
3 years, 10 months ago