

SIMULATION -
You are a penetration tester running port scans on a server.
INSTRUCTIONS -
Part1: Given the output, construct the command that was used to generate this output from the available options.
Part2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part1 -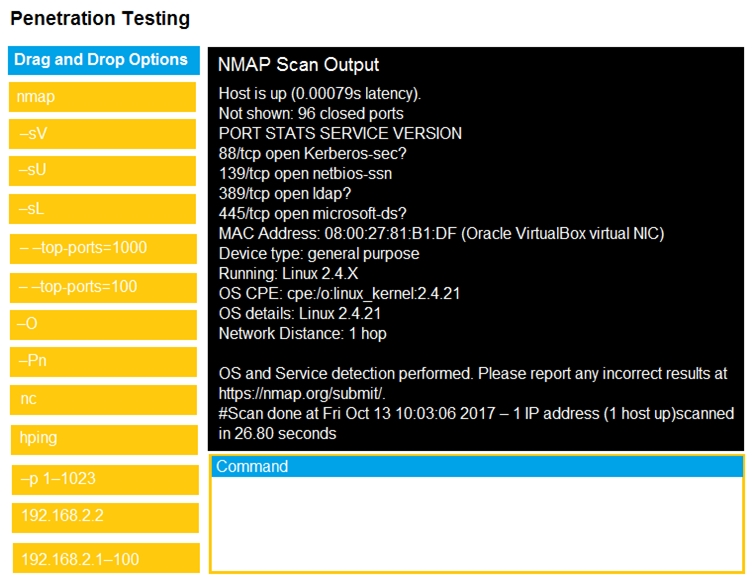
Part2 -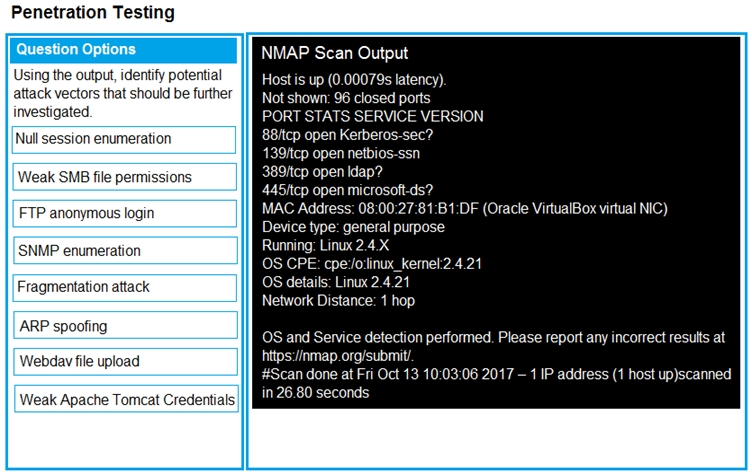
catastrophie
Highly Voted 4 years, 1 month agoBluedegard
1 year, 6 months agohellobob
Highly Voted 4 years, 1 month agoMysterClyde
Most Recent 2 years, 2 months agomiabe
3 years agoCock
3 years, 5 months agoRTFM
3 years, 5 months agoFlowerPowers
3 years, 10 months agoFlowerPowers
3 years, 10 months agolikeahoss
3 years, 9 months agoBluedegard
1 year, 6 months agog4nt3ng
3 years, 11 months agoBill_nye_russian_guy
4 years agohellobob
4 years, 1 month agoCommander123
4 years, 1 month agoxriddle
4 years, 1 month ago