

SIMULATION -
You are a penetration tester running port scans on a server.
INSTRUCTIONS -
Part 1: Given the output, construct the command that was used to generate this output from the available options.
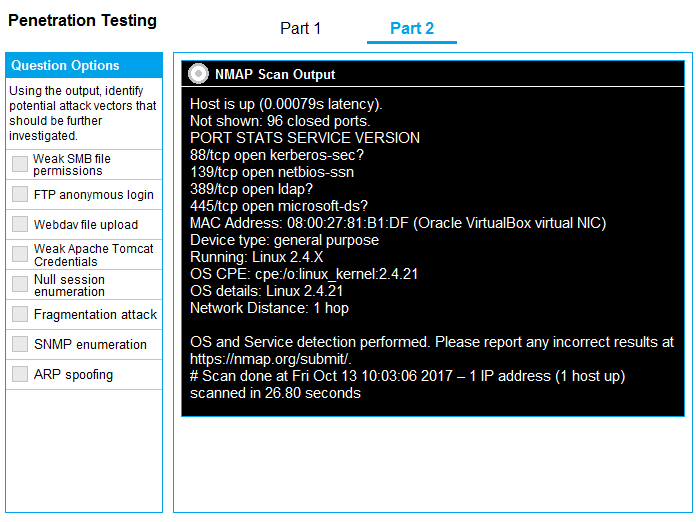
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.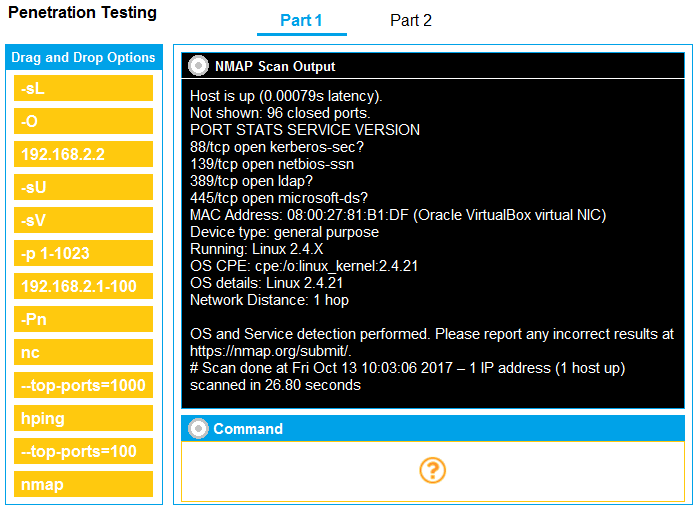
BinarySoldier
Highly Voted 3 years, 8 months agoDavar39
3 years, 7 months agoDavar39
3 years, 7 months agoMeisAdriano
Most Recent 1 year agoMeisAdriano
1 year agoMeisAdriano
1 year agoMeisAdriano
1 year agoRightAsTain
2 years, 10 months agoMeisAdriano
1 year agoshakevia463
3 years agoBostonrock03
3 years, 1 month agoMeisAdriano
1 year agoam2005
3 years, 4 months agoDrChats
3 years, 8 months ago