

An organization recently discovered that spreadsheet files containing sensitive financial data were improperly stored on a web server. The management team wants to find out if any of these files were downloaded by public users accessing the server. The results should be written to a text file and should include the date, time, and IP address associated with any spreadsheet downloads. The web server's log file is named webserver.log, and the report file name should be accessreport.txt. Following is a sample of the web server's log file: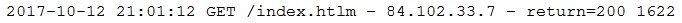
Which of the following commands should be run if an analyst only wants to include entries in which a spreadsheet was successfully downloaded?
R00ted
Highly Voted 2 years, 9 months ago2Fish
2 years, 3 months agoJENNER_ROCKA
Highly Voted 3 years, 3 months agozecomeia_007
Most Recent 11 months, 2 weeks agodavid124
2 years, 5 months agoryanzou
2 years, 9 months agojchutch2
2 years, 9 months agoFastytop
2 years, 10 months agoEVE12
2 years, 10 months agoamateurguy
2 years, 10 months agomiabe
2 years, 11 months agoDavar39
3 years, 2 months agocysa_1127
3 years, 2 months agoXyz_40
3 years, 2 months agothegreatnivram
3 years, 2 months agothegreatnivram
3 years, 2 months agolionleo
3 years, 4 months agoPoopyPants5000
3 years, 5 months ago