

HOTSPOT -
A security analyst suspects that a workstation may be beaconing to a command and control server.
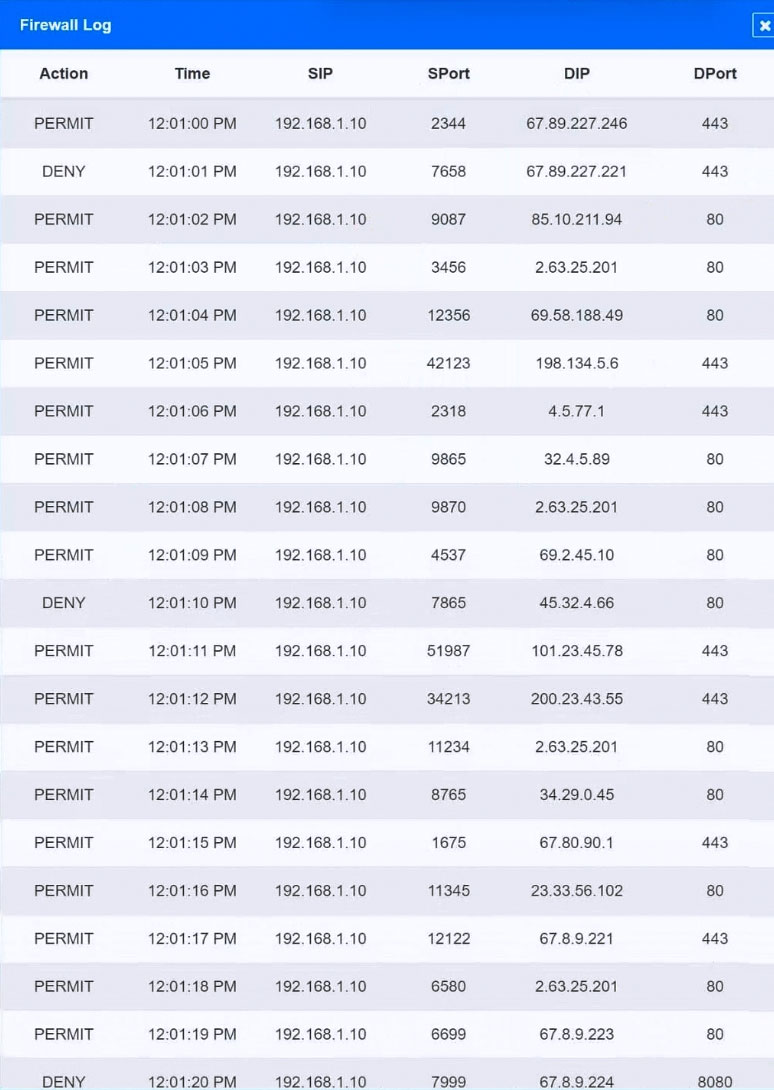
Inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
INSTRUCTIONS -
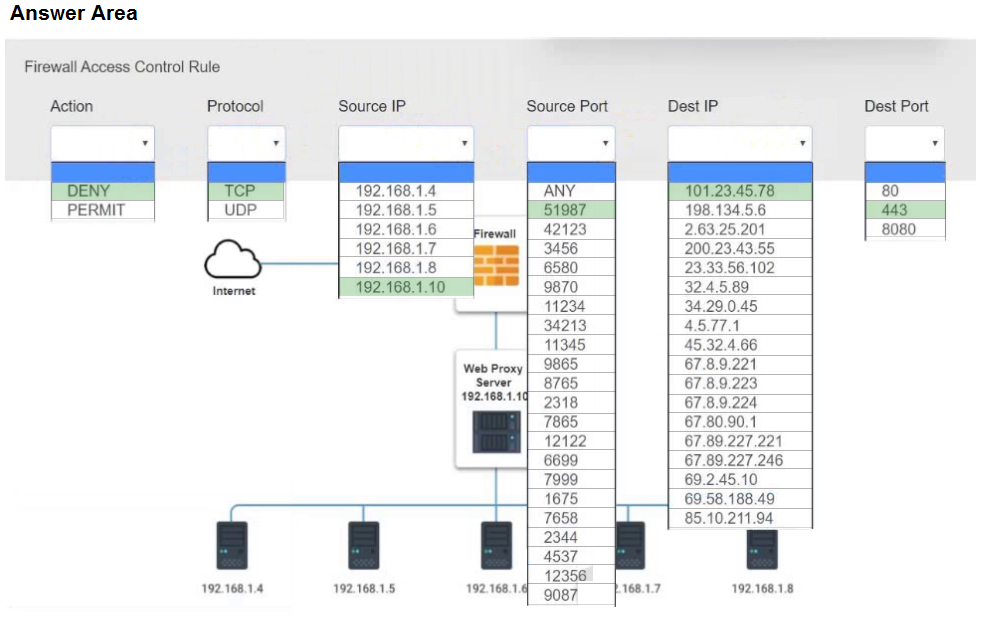
Modify the Firewall Access Control rule to mitigate the issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.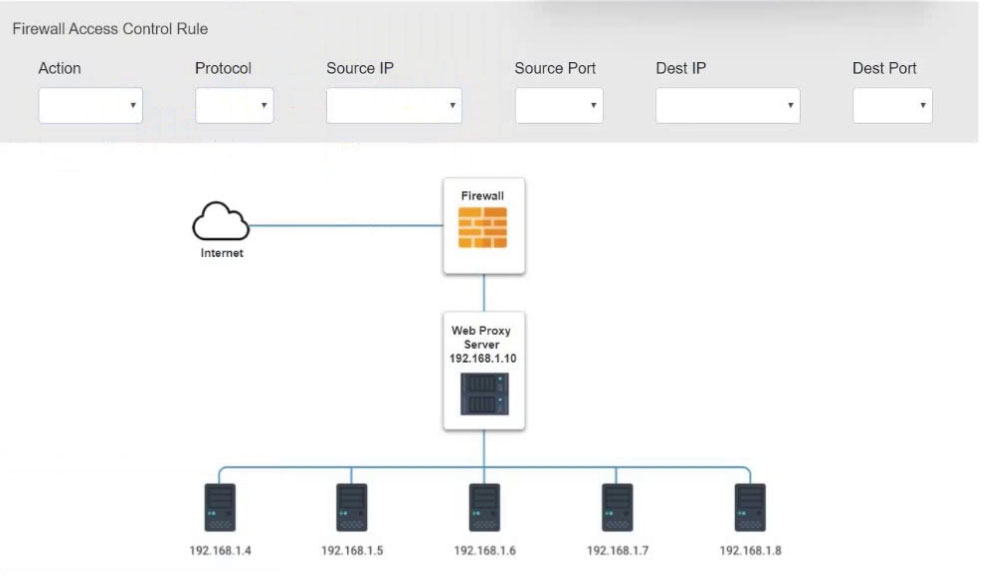

Hot Area: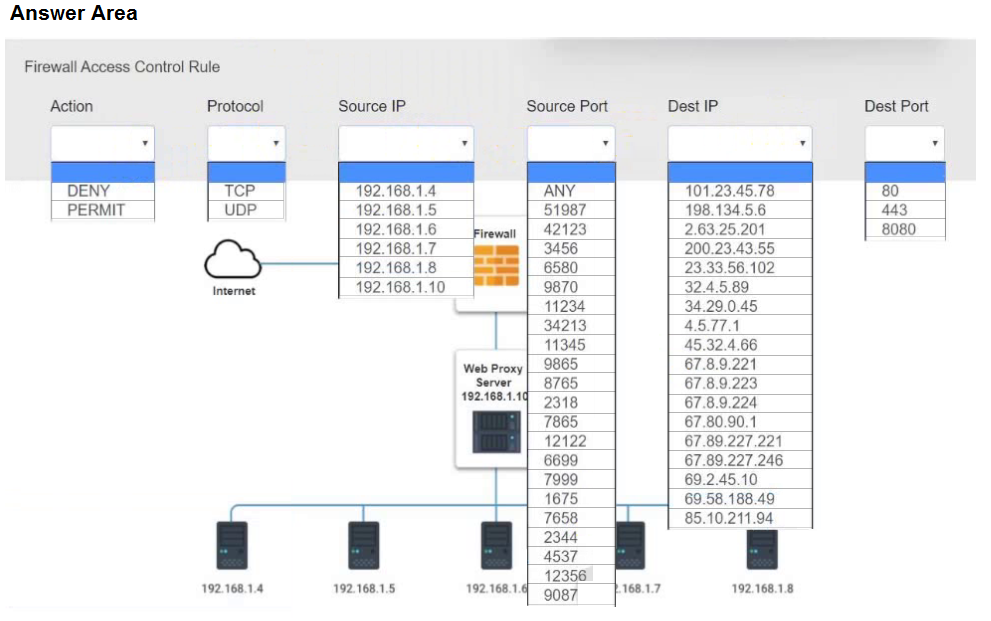
TheSkyMan
Highly Voted 2 years, 9 months agoAaronS1990
2 years, 5 months agojustauser
2 years agoMr_BuCk3th34D
2 years, 6 months ago2Fish
2 years, 3 months agoattesco
1 year, 11 months agoCyberNoob404
Highly Voted 2 years, 5 months agoRT7
Most Recent 1 year, 8 months agoBig_Dre
1 year, 9 months agorg00
1 year, 11 months agoSimonR2
1 year, 11 months agoSimonR2
1 year, 11 months agokiduuu
2 years, 2 months ago[Removed]
2 years, 3 months agoChrisRM
2 years, 4 months agoChrisRM
2 years, 4 months agomsellars
2 years, 7 months agodavid124
2 years, 7 months agoA_core
2 years, 8 months agoCW4901
2 years, 8 months agobigerblue2002
2 years, 9 months agofablus78
2 years, 10 months agotwobuckchuck
2 years, 10 months ago