

A security analyst is running a tool against an executable of an unknown source. The input supplied by the tool to the executable program and the output from the executable are shown below: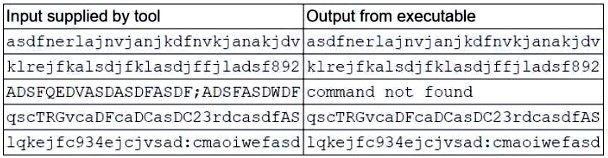
Which of the following should the analyst report after viewing this information?
Bayoneh
1 year, 7 months ago2Fish
2 years, 3 months agoQ23
2 years, 4 months agoAaronS1990
2 years, 4 months agoMrRobotJ
2 years, 7 months agoTascjfbosafj
2 years, 8 months agoR00ted
2 years, 9 months agoadamhoms
2 years, 9 months agononjabusiness
2 years, 9 months agoMerc16
2 years, 9 months agocyberseckid
2 years, 9 months agoTheSkyMan
2 years, 10 months agoLaudy
2 years, 10 months ago