

A security analyst is investigating an incident related to an alert from the threat detection platform on a host (10.0.1.25) in a staging environment that could be running a cryptomining tool because it is sending traffic to an IP address that is related to Bitcoin.
The network rules for the instance are the following: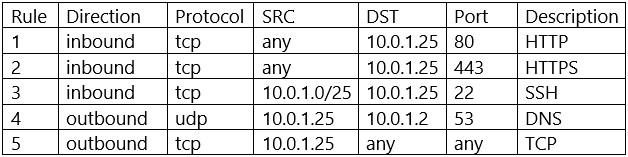
Which of the following is the BEST way to isolate and triage the host?
TheSkyMan
Highly Voted 2 years, 9 months ago2Fish
2 years, 3 months agoLaudy
Highly Voted 2 years, 10 months agocyberseckid
2 years, 9 months agoskibby16
Most Recent 1 year, 7 months agoskibby16
1 year, 10 months agonomad421
2 years agoDutch012
2 years agoCatoFong
2 years, 4 months agoAaronS1990
2 years, 4 months agoCyberNoob404
2 years, 5 months agoSolventCourseisSCAM
2 years, 8 months agoThisGuyStillLearning
2 years, 9 months agoMr_BuCk3th34D
2 years, 6 months agoamateurguy
2 years, 9 months agopiotr3439
2 years, 9 months ago