

A web server has been deployed in a public IaaS provider and has been assigned the public IP address of 72.135.10.100. Users are now reporting that when they browse to the website, they receive a message indicating the service is unavailable. The cloud administrator logs into the server, runs a netstat command, and notices the following relevant output: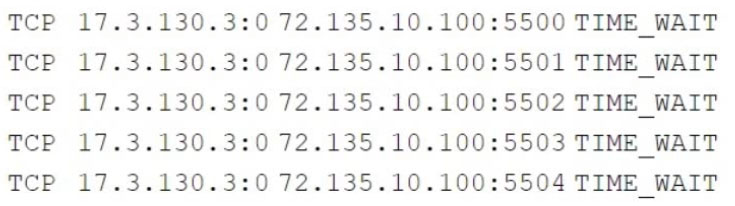
Which of the following actions should the cloud administrator take to resolve the issue?
FrancisDrake
11 months, 3 weeks agoFrancisDrake
11 months, 3 weeks agocobbs
1 year, 4 months agoconcepcionz
1 year, 10 months agomattygster
1 year, 11 months agobeamage
2 years agoFrancisDrake
1 year agoCapJackSparrow
2 years agoNot_That_Guy
2 years, 3 months agoryanzou
2 years, 4 months agojiminycriminal
2 years, 4 months agojiminycriminal
2 years, 4 months agoi_bird
2 years, 4 months agoi_bird
2 years, 4 months ago