

A penetration tester downloaded the following Perl script that can be used to identify vulnerabilities in network switches. However, the script is not working properly.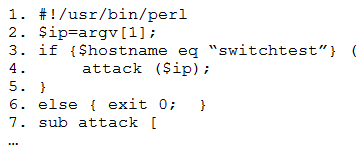
Which of the following changes should the tester apply to make the script work as intended?
som3onenooned1
Highly Voted 1 year, 9 months agoManzer
Highly Voted 1 year, 10 months agoTiredOfTests
Most Recent 9 months, 3 weeks agobieecop
1 year agoKingIT_ENG
1 year, 5 months agonickwen007
1 year, 5 months agokloug
1 year, 6 months agobeamage
1 year, 5 months ago