

Suppose that you test an application for the SQL injection vulnerability. You know that the backend database is based on Microsoft SQL Server. In the login/ password form, you enter the following credentials: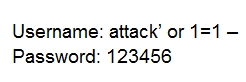
Based on the above credentials, which of the following SQL commands are you expecting to be executed by the server, if there is indeed an SQL injection vulnerability?
Daniel8660
Highly Voted 1 year, 2 months agovictorfs
Most Recent 7 months, 2 weeks agoVOAKDO
11 months, 2 weeks agojosevirtual
1 year, 1 month agokiki533
1 year, 1 month agoC1ph3rSt0rm
1 year, 2 months agokiki533
1 year, 1 month agoAaronS1990
1 year agoShashika90
1 year, 3 months agosn30
1 year, 3 months agonapstervk
1 year, 3 months agoEscltn
1 year, 3 months agoEscltn
1 year, 3 months agoflinux
1 year, 3 months ago