

Refer to the exhibit.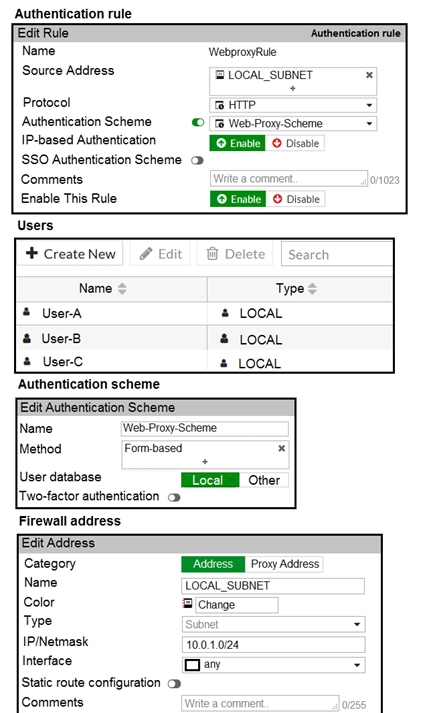
The exhibit shows proxy policies and proxy addresses, the authentication rule and authentication scheme, users, and firewall address.
An explicit web proxy is configured for subnet range 10.0.1.0/24 with three explicit web proxy policies.
The authentication rule is configured to authenticate HTTP requests for subnet range 10.0.1.0/24 with a form-based authentication scheme for the FortiGate local user database. Users will be prompted for authentication.
How will FortiGate process the traffic when the HTTP request comes from a machine with the source IP 10.0.1.10 to the destination http:// www.fortinet.com? (Choose two.)
sahilk
Highly Voted 3 years, 10 months agokkkvo
3 years, 10 months agoCarol254
3 years, 6 months agothissiteisgreat
Highly Voted 4 years agocessyang
4 years agoEist
Most Recent 1 year, 9 months agoJuanTrabal
3 years agomesql
3 years agoSandroAlex
3 years, 4 months agoxYanivDx
3 years, 5 months agoScottXYZ
3 years, 7 months agoSeph1
3 years, 10 months ago2021gene
3 years, 10 months ago