
Expert Verified, Online, Free.

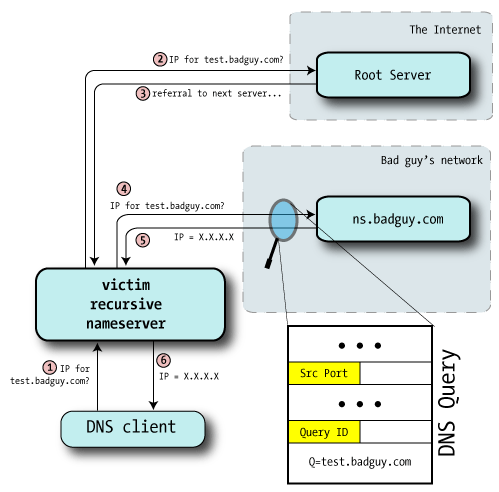
attacker.evil.org is attempting to insert a poisoned cache entry for www.moneybags on the dns.victim.com DNS server using the Kaminsky method of DNS cache poisoning. Of the following choices, which would be an example of an effective query sent by the attacker?
strale
1 month ago