

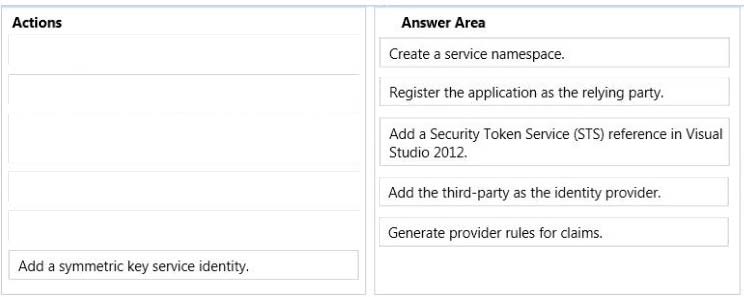
DRAG DROP -
You are developing an ASP.NET MVC application that allows users to log on by using a third-party authenticator.
You need to configure Microsoft Azure Access Control Services and the application.
Which five actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Select and Place:
founderDev
Highly Voted 5 years, 4 months agoilCorvo
5 years, 4 months agoKarel_Gott
5 years, 2 months agoshyams3382
Most Recent 4 years, 6 months agohungry_ape9000
5 years, 1 month ago