

DRAG DROP -
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario -
You are developing a Microsoft Azure SQL data warehouse to perform analytics on the transit system of a city. The data warehouse will contain data about customers, trips, and community events.
You have two storage accounts named StorageAccount1 and StorageAccount2. StorageAccount1 is associated to the data warehouse. StorageAccount2 contains weather data files stored in the CSV format. The files have a naming format of city_state_yyymmdd.csv.
Microsoft SQL Server is installed on an Azure virtual machine named AzureVM1.
You are migrating from an existing on premises solution that uses Microsoft SQL Server 2016 Enterprise. The planned schema is shown in the exhibit. (Click the
Exhibit button)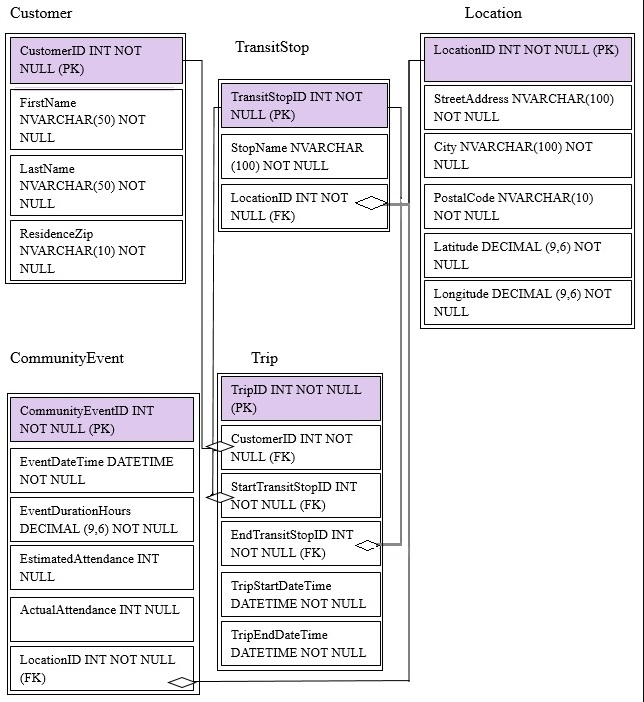
The first column of each table will contain unique values. A table named Customer will contain 12 million rows. A table named Trip will contain 3 billion rows.
You have the following view.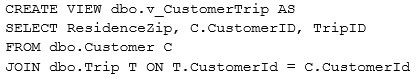
You plan to use Azure Data Factory to perform the following four activities:
✑ Activity1: Invoke an R script to generate a prediction column.
✑ Activity2: Import weather data from a set of CSV files in Azure Blob storage
✑ Activity3: Execute a stored procedure in the Azure SQL data warehouse.
✑ Activity4: Copy data from an Amazon Simple Storage Service (S3).
You plan to detect the following two threat patterns:
✑ Pattern1: A user logs in from two physical locations.
✑ Pattern2: A user attempts to gain elevated permissions.
End of repeated scenario -
Which types of threat detection should you configure for each threat pattern? To answer, drag the appropriate threat detection types to the correct patterns. Each threat detection type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

Comments