

You have an Azure subscription that contains an Azure key vault named KeyVault1 and the virtual machines shown in the following table.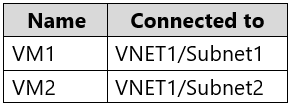
KeyVault1 has an access policy that provides several users with Create Key permissions.
You need to ensure that the users can only register secrets in KeyVault1 from VM1.
What should you do?
Deepbond
Highly Voted 4 years, 6 months agogssd4scoder
4 years, 1 month agoBrettusMaximus
4 years agoGulam
4 years agominihere
3 years, 5 months agoOmerBeyond
4 years, 6 months agoGranwizzard
4 years, 5 months agojank
4 years, 4 months agojank
4 years, 4 months agokubinho
4 years, 1 month agoAghora
Highly Voted 4 years, 5 months agoQiangQiang
4 years, 2 months agokvsaheed
Most Recent 3 years, 3 months ago[Removed]
3 years, 4 months agoritears41
3 years, 4 months agoAberdeenAngus
3 years, 4 months agoJayBee65
3 years, 5 months agoazurelearner666
3 years, 5 months agovalgaw
3 years, 6 months agothebarber87
3 years, 6 months agoJayBee65
3 years, 5 months agoFartfart
3 years, 6 months agoDawn7
3 years, 6 months agogcpbrig01
3 years, 7 months agoDpejic
3 years, 7 months agoedmacoar123
3 years, 7 months agoHiAws
3 years, 9 months agoThisismynickname001
3 years, 10 months ago