

HOTSPOT -
You have a Microsoft 365 E5 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com.
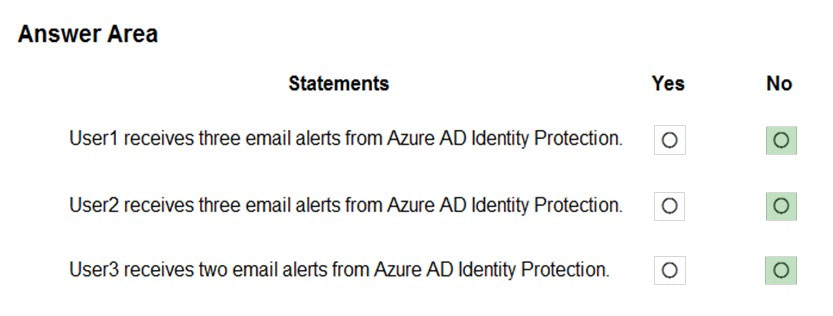
Azure AD Identity Protection alerts for contoso.com are configured as shown in the following exhibit.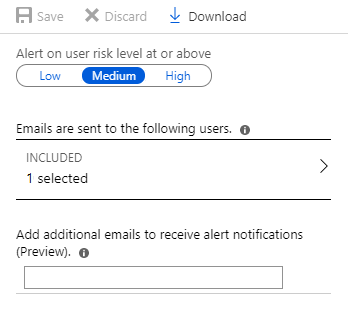
A user named User1 is configured to receive alerts from Azure AD Identity Protection.
You create users in contoso.com as shown in the following table.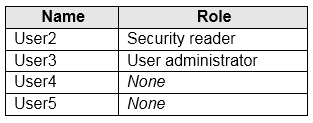
The users perform the sign-ins shown in the following table.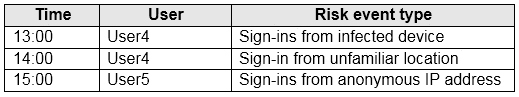
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: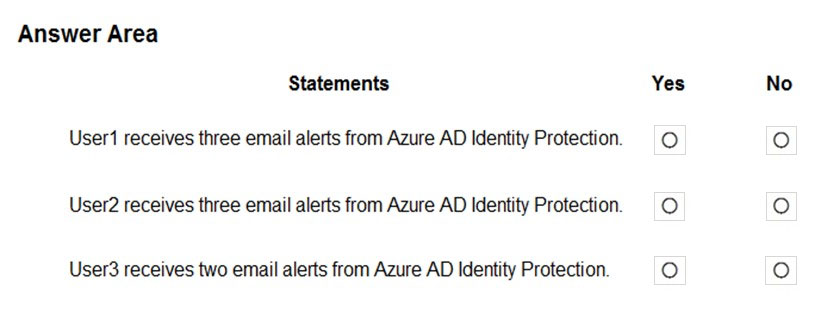
kiketxu
Highly Voted 4 years, 3 months agoSethoo
4 years, 3 months agoTheGuy
4 years, 3 months agoKalzonee3611
4 years, 1 month agoJhill777
3 years, 1 month agoYetijo
4 years agoMrAce
Highly Voted 3 years, 10 months agokidney83
3 years, 9 months agoGrudo
3 years, 5 months agoRVR
2 years, 9 months agoGatesBill
Most Recent 2 years, 2 months agoSKam22
2 years, 11 months agoWhatsamattr81
2 years, 11 months agombecile
3 years, 5 months agomkoprivnj
3 years, 7 months agoRstilekar
3 years, 7 months agoadamsca
3 years, 8 months agogkp_br
3 years, 8 months agoAlexanderSaad
3 years, 9 months agoHami3191
3 years, 9 months agoThe_Poet
3 years, 11 months agoThBEST
3 years, 11 months agoDestny
4 years, 1 month agoPitch09
4 years, 1 month agoismossss
4 years, 1 month ago