

HOTSPOT -
Your network contains an on-premises Active Directory domain named adatum.com that syncs to Azure Active Directory (Azure AD) by using the Azure AD
Connect Express Settings. Password writeback is disabled.
You create a user named User1 and enter Pass in the Password field as shown in the following exhibit.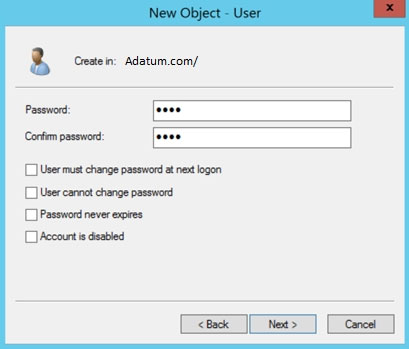
The Azure AD password policy is configured as shown in the following exhibit.
Hot Area: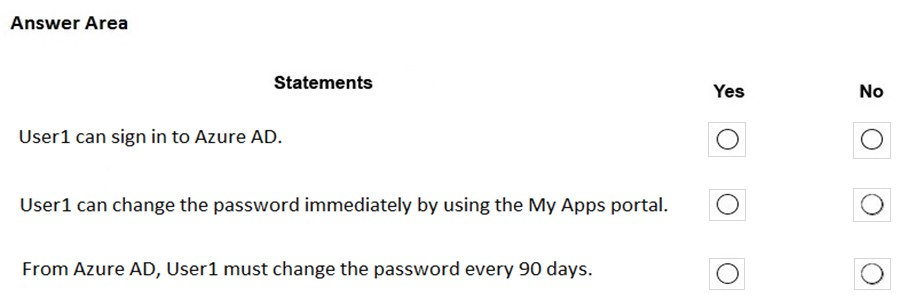
TheWallPTA
Highly Voted 4 years, 2 months agoBoxGhost
3 years, 2 months agoadaniel89
Highly Voted 4 years agoBobalo
3 years, 11 months agoAmir1909
Most Recent 1 year, 4 months agoMeebler
2 years, 3 months agoEverlastday
2 years, 5 months agoModerator
2 years, 10 months agoModerator
2 years, 11 months agoContactfornitish
2 years, 11 months agoTechMinerUK
3 years agotrexar
3 years, 2 months agoKSvh53
3 years, 3 months agoDurden871
3 years, 4 months agoDurden871
3 years, 4 months agoDurden871
3 years, 4 months agoStorm
3 years, 5 months agojkklim
3 years, 6 months agolengySK
3 years, 10 months agoemilianogalati
3 years, 10 months agoemilianogalati
3 years, 9 months agoAZalan
3 years, 11 months ago