

HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.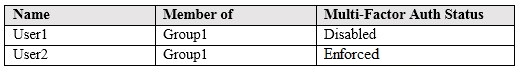
Multi-factor authentication (MFA) is configured to use 131.107.5.0/24 as trusted IPs.
The tenant contains the named locations shown in the following table.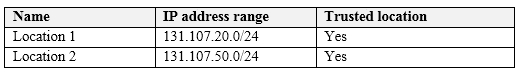
You create a conditional access policy that has the following configurations:
✑ Users and groups assignment: All users
✑ Cloud apps assignment: App1
✑ Conditions: Include all trusted locations
✑ Grant access: Require multi-factor authentication
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: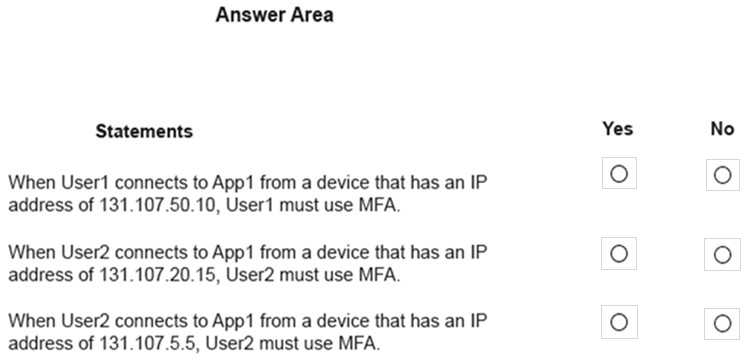
Gus01
Highly Voted 4 years, 2 months agomitsios96
3 years, 9 months agoJ0J0
4 years agoPaolo2022
2 years, 7 months agoqhuy199
1 year, 5 months agorfox321
3 years, 8 months agoStorm
3 years, 5 months agoBoxGhost
3 years, 2 months agomorito
3 years agoprepre
Highly Voted 4 years, 2 months agoOne111
2 years, 6 months agoOne111
Most Recent 1 year, 9 months agojustabasicuser
2 years, 2 months agoFeyenoord
2 years, 3 months agoEverlastday
2 years, 5 months agoStartkabels
2 years, 6 months agobill1982
2 years, 11 months agoStiobhan
3 years agoNilz76
3 years, 2 months agoIamrandom
3 years, 5 months agokanag1
3 years, 5 months agofko1978
3 years, 9 months agoStorm
3 years, 5 months agoNico95
3 years, 10 months agoitmaster
3 years, 2 months agospg987
3 years, 10 months agoNasser
3 years, 10 months agoStorm
3 years, 5 months agomelatocaroca
4 years, 1 month agojosepedroche
2 years, 4 months ago