

You have the following advanced hunting query in Microsoft 365 Defender.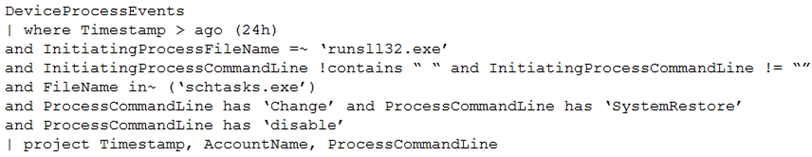
You need to receive an alert when any process disables System Restore on a device managed by Microsoft Defender during the last 24 hours.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
teehex
Highly Voted 9 months, 4 weeks agoArciOfficial
Highly Voted 4 years agoim20batman
1 year, 7 months agonk_exam
Most Recent 8 months, 1 week agoNikki0222
8 months, 4 weeks agoMetasploit
9 months, 4 weeks agoOryx360
9 months, 4 weeks agosmanzana
1 year, 5 months agochepeerick
1 year, 9 months agoP0wned
1 year, 9 months agoJuNanski
2 years, 3 months agoApocalypse03
2 years, 7 months agoFukacz
2 years, 10 months agoTx4free
3 years, 4 months agoliberty123
3 years, 5 months agostromnessian
3 years, 5 months agostromnessian
3 years, 5 months agoHacker00
3 years, 6 months ago