

Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an app named App1 that is installed on two Azure virtual machines named VM1 and VM2. Connections to App1 are managed by using an Azure Load
Balancer.
The effective network security configurations for VM2 are shown in the following exhibit.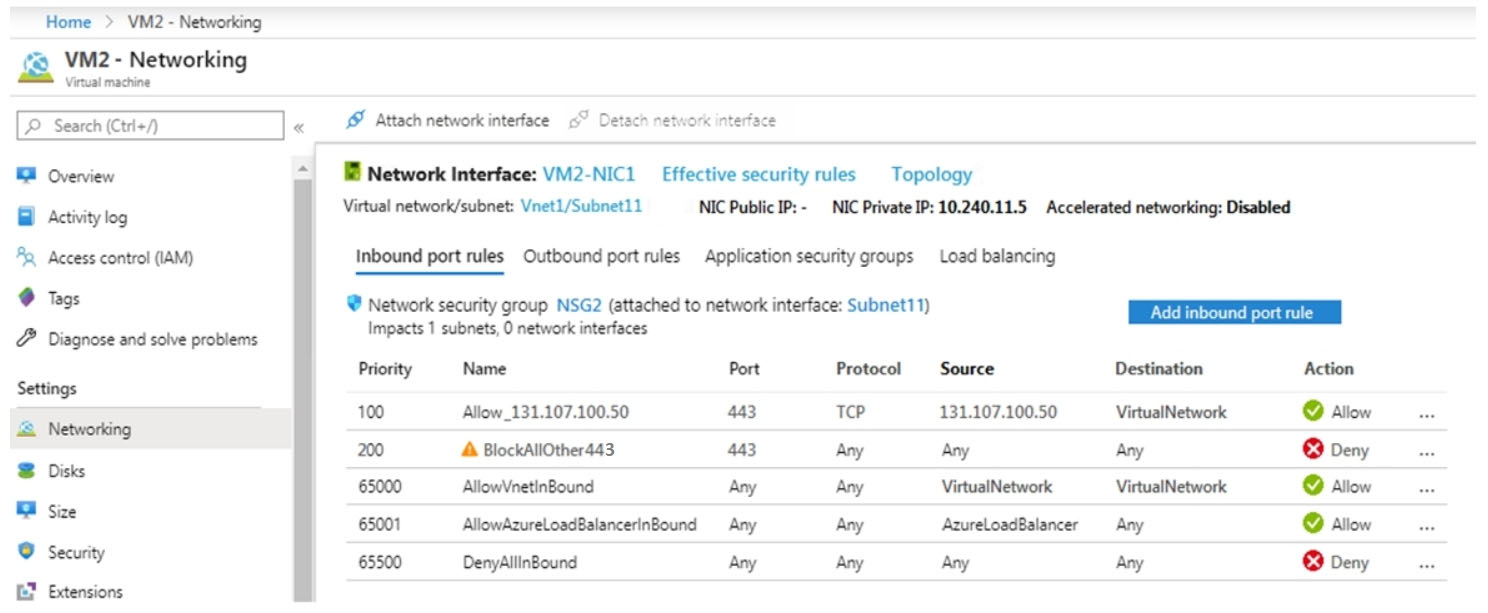
You discover that connections to App1 from 131.107.100.50 over TCP port 443 fail.
You verify that the Load Balancer rules are configured correctly.
You need to ensure that connections to App1 can be established successfully from 131.107.100.50 over TCP port 443.
Solution: You create an inbound security rule that allows any traffic from the AzureLoadBalancer source and has a cost of 150.
Does this meet the goal?
Bursuc03
Highly Voted 4 years, 1 month agoAbubaker3030
3 years, 1 month agoDurden871
2 years, 3 months agodjhyfdgjk
1 year, 4 months agonzalex1
3 years, 8 months agosuryamk
3 years agoDurden871
2 years, 3 months agodarsy2001
Highly Voted 4 years, 1 month agombravo
4 years, 1 month agoorion1024
3 years, 9 months agoboyzz
3 years, 2 months agos9p3r7
4 years agoukivanlamlpi
2 years, 4 months agoNathan12345
Most Recent 4 months, 2 weeks agoDankho
8 months, 3 weeks ago87dffd4
11 months, 3 weeks agoVICEROY
1 year agoCharlesS76
1 year, 1 month agoaikooo
1 year, 3 months agoRemmyT
1 year, 3 months agoRemmyT
1 year, 3 months agobobothewiseman
1 year, 3 months agoBlueee
1 year, 4 months agojhodax
1 year, 4 months agobelyo
1 year, 5 months agoamsioso
1 year, 6 months agonchebbi
1 year, 7 months agonchebbi
1 year, 7 months agoMOSES3009
1 year, 7 months ago