

HOTSPOT -
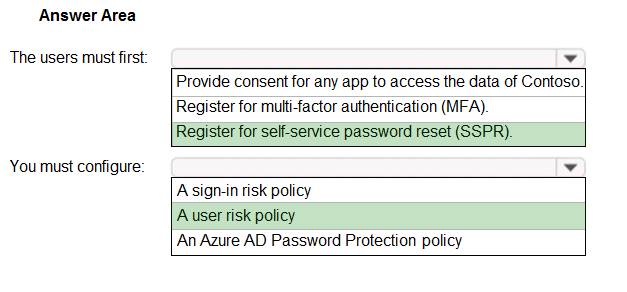
You need to meet the technical requirements for the probability that user identities were compromised.
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: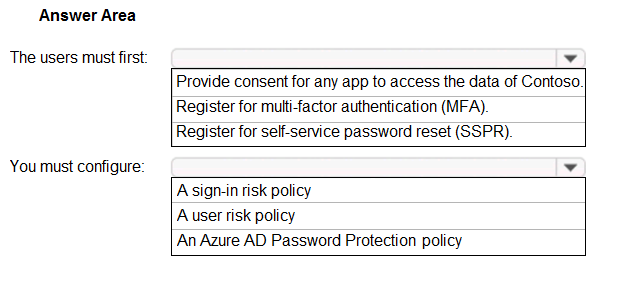
DPRamone
Highly Voted 4 years ago007Ali
3 years, 5 months agodensyo
Highly Voted 3 years, 8 months agoBorbz
3 years, 7 months agothetootall
Most Recent 11 months, 1 week agoSneekygeek
1 year, 4 months agodule27
1 year, 11 months agowsrudmen
2 years, 4 months agoFaheem2020
2 years, 8 months agow00t
2 years, 9 months agoFaheem2020
2 years, 9 months agosapien45
2 years, 11 months agoRandomNickname
3 years agoXyz_40
3 years agoYelad
3 years, 2 months agoJun143
3 years, 3 months agoTheGuy
3 years, 3 months agostromnessian
3 years, 3 months agostromnessian
3 years, 3 months ago