

HOTSPOT -
You have a Microsoft 365 E5 subscription.
You plan to perform cross-domain investigations by using Microsoft 365 Defender.
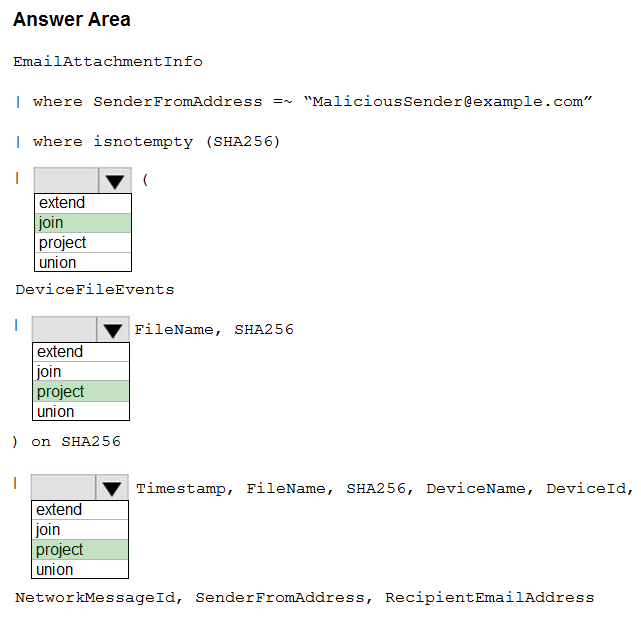
You need to create an advanced hunting query to identify devices affected by a malicious email attachment.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: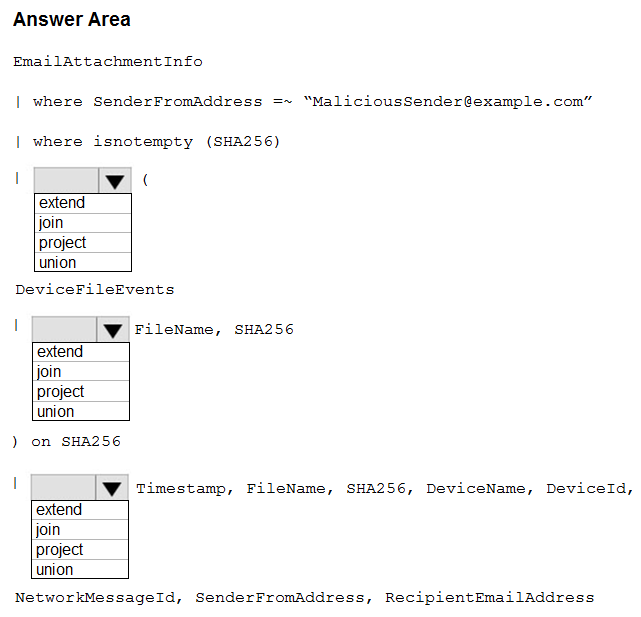
teehex
Highly Voted 4 years, 2 months agoJoeP1
2 years agoPJR
Highly Voted 10 months, 1 week agoDigitalNomad
3 years, 9 months agoContactfornitish
3 years, 5 months agoContactfornitish
3 years, 5 months agoarcausbd
1 year, 10 months agoNikki0222
Most Recent 9 months, 2 weeks agoApocalypse03
10 months, 1 week ago0610fcd
10 months, 1 week agoKTM_999
10 months, 1 week agoscfitzp
1 year ago4b097e5
1 year, 1 month agoemartiy
1 year, 1 month agoemartiy
1 year, 1 month agoHarryd82
1 year, 3 months agoae88d96
1 year, 5 months agosmanzana
1 year, 8 months agomb0812
1 year, 5 months agobillo79152718
2 years agodonathon
2 years agoUser_Mowgli
2 years, 9 months agodanb67
2 years, 11 months agoMetasploit
2 years, 9 months agogyaansastra
2 years, 7 months agodanb67
1 year, 9 months agodanb67
1 year, 9 months agoShubham020
3 years, 4 months ago