

DRAG DROP -
You need to increase the security of your team's development process.
Which type of security tool should you recommend for each stage of the development process? To answer, drag the appropriate security tools to the correct stages. Each security tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: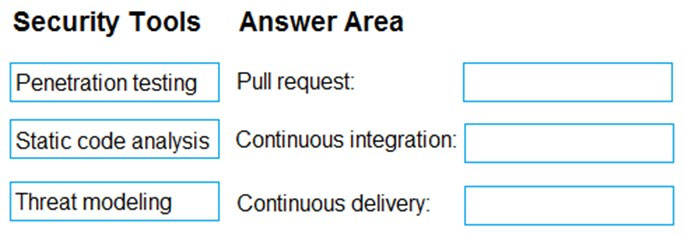
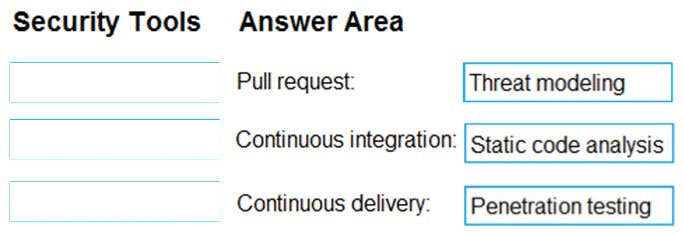
rengs
Highly Voted 4 years agordemontis
3 years, 3 months agoZodiaC
3 years, 12 months agoPlumpyTumbler
Highly Voted 3 years, 5 months agoxRiot007
1 year, 11 months agoozbonny
Most Recent 1 year, 4 months agoozbonny
1 year, 4 months agoozbonny
1 year, 4 months agoCirusD
1 year, 9 months agoyana_b
1 year, 11 months agoieboaix
1 year, 11 months agozellck
2 years, 1 month agodmeld
2 years, 8 months agoMattt
1 year, 1 month agosyu31svc
2 years, 11 months agoGovcomm
2 years, 11 months agoInland
3 years agoEltooth
3 years, 1 month agoCheehp
3 years, 2 months agod0bermannn
3 years, 9 months agosanhoo
3 years, 11 months agoxRiot007
1 year, 11 months ago