

HOTSPOT -
You have a Microsoft 365 E5 subscription that uses Microsoft Defender and an Azure subscription that uses Azure Sentinel.
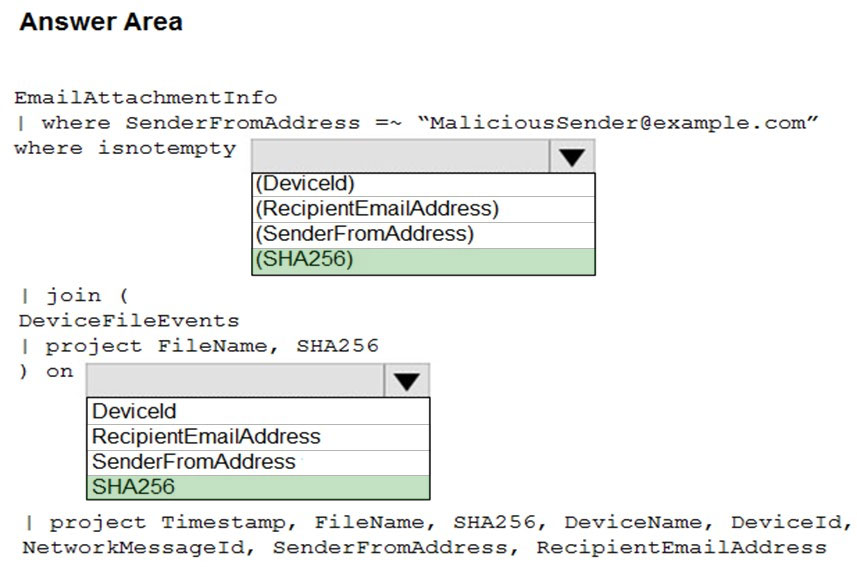
You need to identify all the devices that contain files in emails sent by a known malicious email sender. The query will be based on the match of the SHA256 hash.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: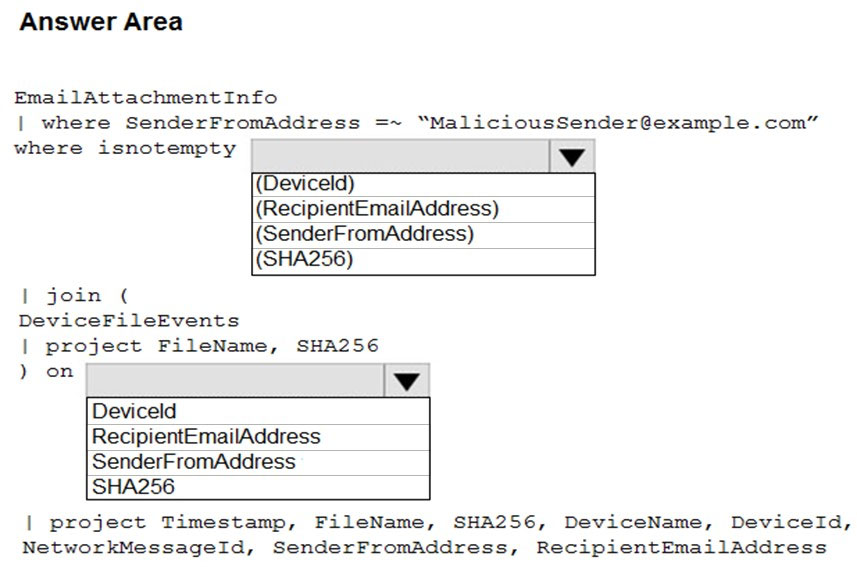
HSBNZ
Highly Voted 3 years, 10 months agoMetasploit
2 years, 8 months agoRamye
1 year, 3 months agoApocalypse03
Highly Voted 2 years, 6 months agoNikki0222
Most Recent 8 months agochepeerick
1 year, 8 months agotrashbox
1 year, 9 months ago