

HOTSPOT -
You have a Microsoft 365 tenant.
You need to identify users who have leaked credentials. The solution must meet the following requirements:
✑ Identify sign-ins by users who are suspected of having leaked credentials.
✑ Flag the sign-ins as a high-risk event.
✑ Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: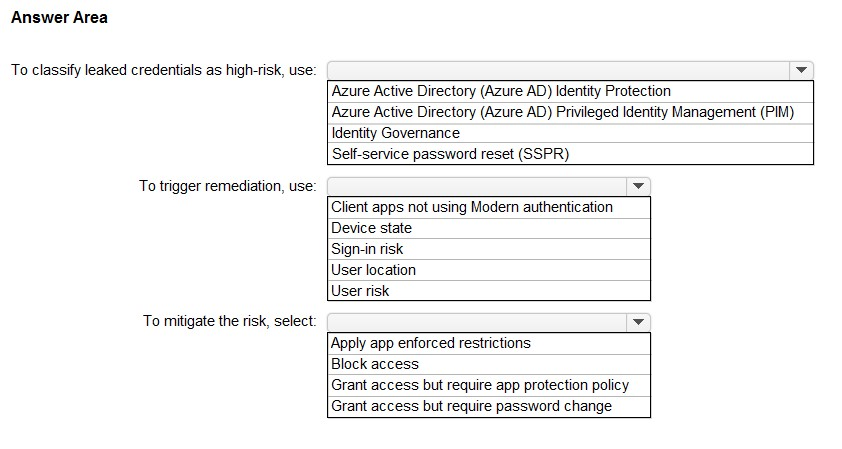
abelchior
Highly Voted 3 years, 11 months agoBaderJ
Highly Voted 3 years, 10 months agoAdemola_12
Most Recent 1 year, 5 months agoTuvshinjargal
1 year, 6 months agocsi_2025
5 months, 2 weeks agoTony416
11 months, 2 weeks agoEmnCours
2 years agoHeshan
2 years, 1 month agodule27
2 years, 1 month agochrisp1992
2 years, 8 months agoZubairr13
3 years agorachee
3 years, 1 month agoXyz_40
3 years, 2 months agoJun143
3 years, 4 months agoBluediamond
3 years, 5 months agoBluediamond
3 years, 5 months agoPravda
3 years, 6 months ago