

HOTSPOT -
A company deploys several model-driven apps. The company uses shared devices in their warehouse. The devices are always powered on. Users log on to the devices and then launch the apps to perform actions.
Unauthorized users recently uploaded several files after another user failed to log out of a device. The company needs to prevent these incidents from occurring in the future.
You need to configure the solution to prevent the reported security incidents.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: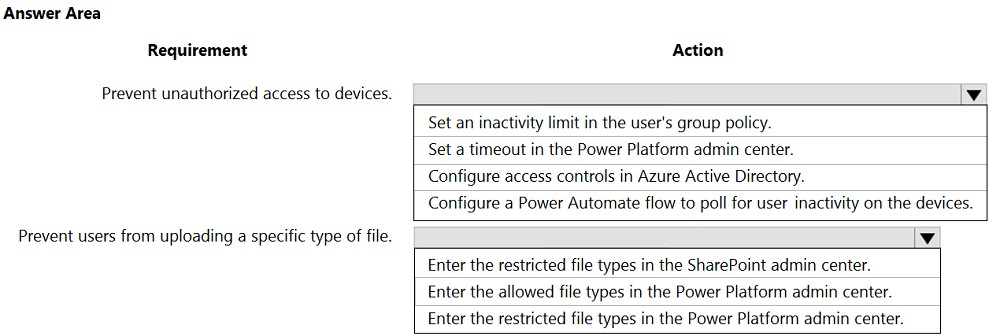

imbaster
Highly Voted 3 years, 11 months agoWalterddd
3 years, 3 months agoWalterddd
3 years, 3 months agoandy365
2 years, 1 month agogerbendenboer
Highly Voted 3 years, 11 months agoAbokhate
Most Recent 1 month, 2 weeks agoChristoz
2 months agoMVPConsultant
1 year agoLRRooster
1 year, 1 month agoWikyWik
1 year, 4 months agosolidshag
1 year, 6 months agoSri2020
1 year, 6 months agogina_the_boss
1 year, 6 months agowajid124
1 year, 11 months agoinzagi
2 years agoAero_1898
2 years agoLeylae
2 years, 8 months agoinespal
2 years, 2 months agouberlord
2 years agoMrEz
1 year, 5 months agoMoazzamBhuian
2 years, 10 months agoNakom
2 years, 10 months agoAdyK
2 years, 11 months ago