

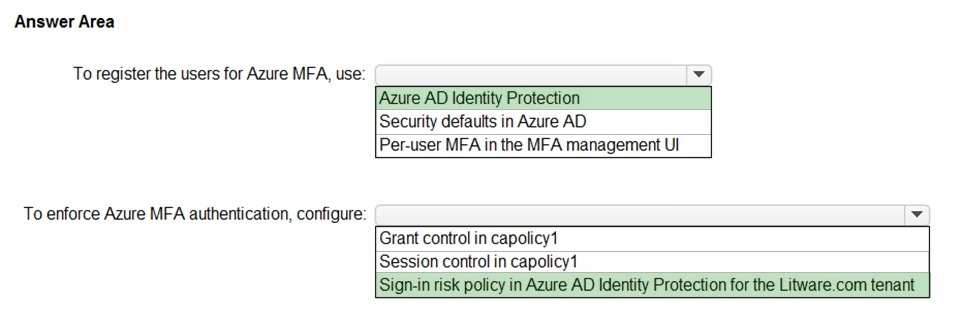
HOTSPOT -
You need to ensure that users managing the production environment are registered for Azure MFA and must authenticate by using Azure MFA when they sign in to the Azure portal. The solution must meet the authentication and authorization requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
pentium75
Highly Voted 3 years, 9 months agoMTK94
3 years, 9 months agoleo_az300
3 years, 8 months agostudent22
Highly Voted 3 years, 7 months agoRepohunter
Most Recent 3 years agoAberdeenAngus
2 years, 11 months agoDpejic
3 years, 5 months agosyu31svc
3 years, 8 months agopoplovic
3 years, 8 months agoleo_az300
3 years, 8 months agonkv
3 years, 8 months agoravi000001
3 years, 9 months agojjdevine
3 years, 9 months agoJ4U
3 years, 9 months ago