

DRAG DROP -
You plan to use containerized versions of the Anomaly Detector API on local devices for testing and in on-premises datacenters.
You need to ensure that the containerized deployments meet the following requirements:
✑ Prevent billing and API information from being stored in the command-line histories of the devices that run the container.
✑ Control access to the container images by using Azure role-based access control (Azure RBAC).
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
Select and Place: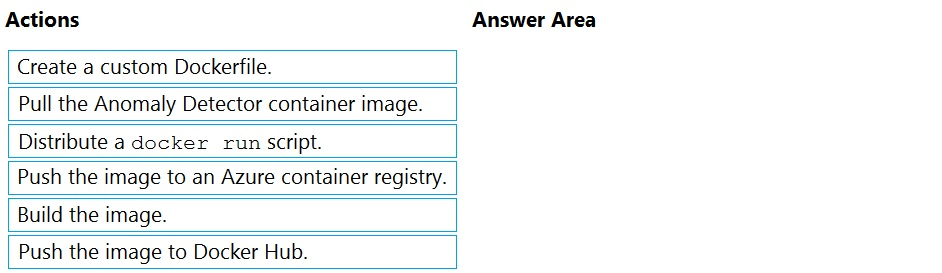

dinhhungitsoft
Highly Voted 3 years, 1 month agoAouatef
11 months, 2 weeks agosheldon73
2 years agommaguero
Highly Voted 9 months agoserj
11 months, 2 weeks agordemontis
1 year, 7 months agoanto69
1 year, 5 months agosyupwsh
Most Recent 4 months, 1 week agoMASANASA
6 months, 2 weeks agoangelrishi
7 months, 3 weeks agoSAMBIT
9 months agoRahulShahane
9 months agoAzureGeek79
9 months, 1 week agotestmaillo020
10 months agoRahulShahane
10 months, 1 week agorookiee1111
1 year agonanaw770
1 year, 1 month agoTJ001
1 year, 1 month agomiai74uu
4 months, 2 weeks agoTJ001
1 year, 1 month agoTJ001
1 year agotolliik
1 year, 1 month agovovap0vovap
1 year agovarinder82
1 year, 3 months agoMurtuza
1 year, 3 months ago