

DRAG DROP -
You are implementing conditional access policies.
You must evaluate the existing Azure Active Directory (Azure AD) risk events and risk levels to configure and implement the policies.
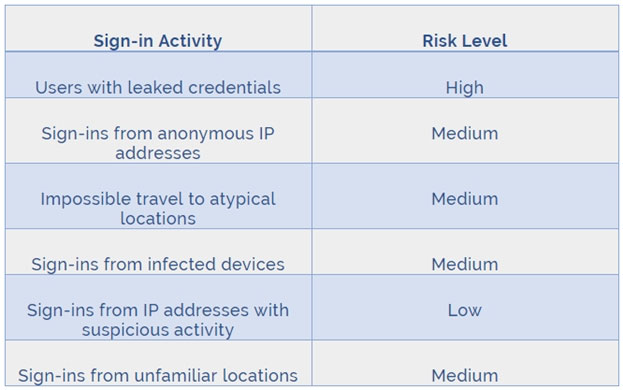
You need to identify the risk level of the following risk events:
✑ Users with leaked credentials
✑ Impossible travel to atypical locations
✑ Sign-ins from IP addresses with suspicious activity
Which level should you identify for each risk event? To answer, drag the appropriate levels to the correct risk events. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:


majstor86
Highly Voted 2 years, 4 months agoMalikusmanrasheed
2 years, 1 month agoahorva
Highly Voted 3 years, 1 month agoPowerBIAddict
3 years, 1 month agostonwall12
Most Recent 4 months, 2 weeks agotrashbox
1 year, 8 months agoAndre369
2 years, 1 month agoxRiot007
11 months, 2 weeks agoIvanIco
1 year, 9 months agoFonKeel
2 years, 5 months agoawfnewf1q243
2 years, 8 months agothe_flow88
2 years, 11 months agophi3nix
3 years, 1 month ago