

You create an Azure Sentinel workspace.
You configure Azure Sentinel to ingest data from Azure Active Directory (Azure AD).
In the Azure Active Directory admin center, you discover Azure AD Identity Protection alerts. The Azure Sentinel workspace shows the status as shown in the following exhibit.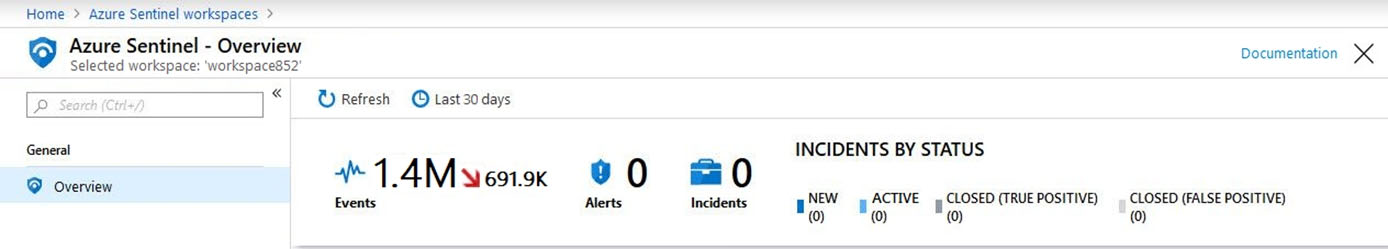
In Azure Log Analytics, you can see Azure AD data in the Azure Sentinel workspace.
What should you configure in Azure Sentinel to ensure that incidents are created for detected threats?
heshmat2022
Highly Voted 2 years, 9 months agoKing_Khong
Most Recent 2 years, 3 months agoshouro88
2 years, 5 months agoWedge34
2 years, 8 months agoAcbrownit
2 years, 5 months agoRVR
2 years, 9 months agoheshmat2022
2 years, 9 months ago