

HOTSPOT -
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains servers that run Windows Server as shown in the following table.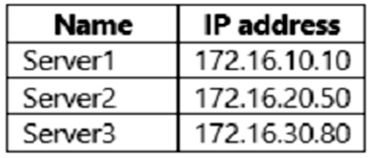
Server1 has the connection security rules shown in the following table.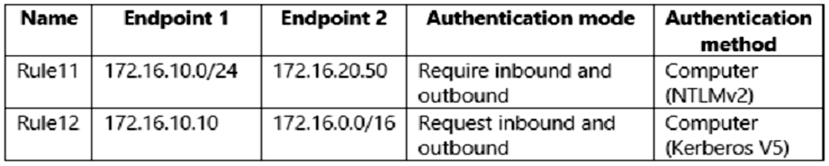
Server2 has the connection security rules shown in the following table.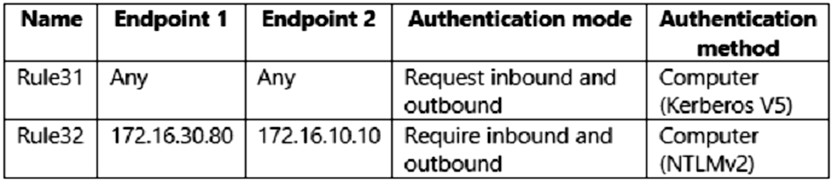
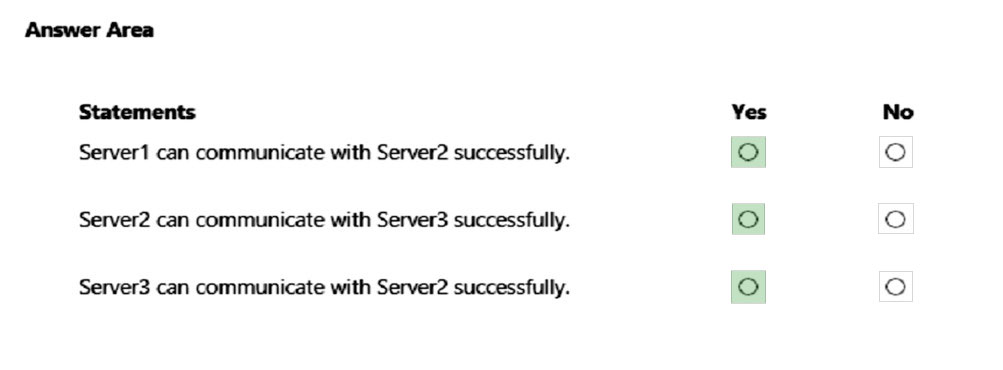
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: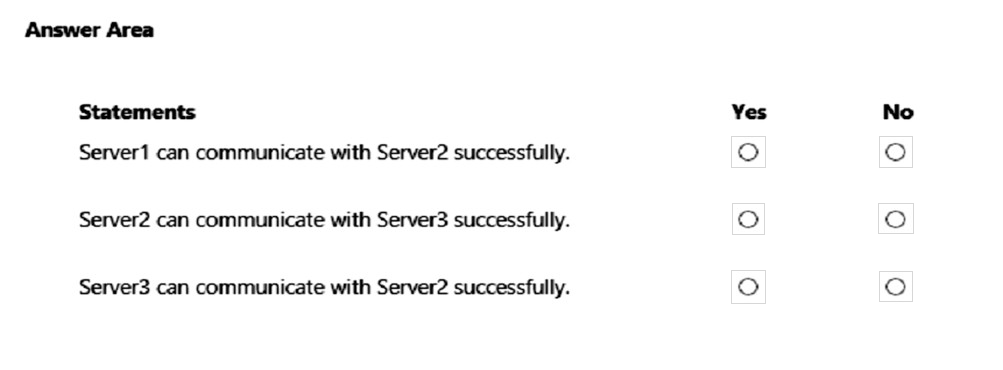
Lu5ck
Highly Voted 2 years, 4 months agoLeocan
Highly Voted 2 years, 5 months agoBlackCat9588
Most Recent 4 months, 1 week agoRemmyT
10 months, 2 weeks agosmorar
1 year agoSlavekJ
1 year, 8 months agocalotta1
1 year, 10 months agoKakashiCopyNinja
1 year, 11 months agosyu31svc
2 years, 1 month agosyu31svc
2 years, 1 month agoSTFN2019
2 years, 2 months agocris66
2 years, 3 months agocris66
2 years, 3 months agocris66
2 years, 3 months agojecawi9630
2 years, 4 months agocris66
2 years, 5 months agocris66
2 years, 5 months agorimvydukas
2 years, 5 months agojoehoesofat
2 years, 6 months ago