

HOTSPOT -
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You need to create a policy that will generate an email alert when a banned app is detected requesting permission to access user information or data in the subscription.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: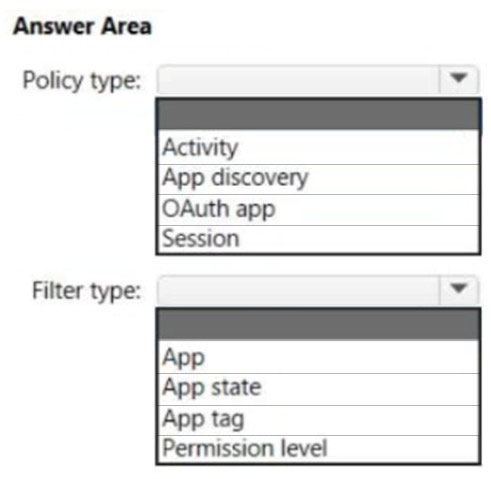
bac0n
Highly Voted 2 years, 6 months agoJakeLi
2 years, 5 months agoNitishKarmakar
Most Recent 1 year, 9 months agoKees1990
2 years, 3 months agorenrenren
2 years, 3 months agoMeebler
2 years, 3 months agoMeebler
2 years, 3 months agoMeebler
2 years, 3 months agoEsamiTopici
2 years, 4 months agoreastman66
2 years, 8 months ago