

Identify the API that is not supported by Check Point currently.
Correct Answer:
C
🗳️
SandBlast Mobile identifies threats in mobile devices by using on-device, network, and cloud-based algorithms and has four dedicated components that constantly work together to protect mobile devices and their data. Which component is NOT part of the SandBlast Mobile solution?
Correct Answer:
C
🗳️
Reference:
https://community.checkpoint.com/docs/DOC-3072-sandblast-mobile-architecture-overview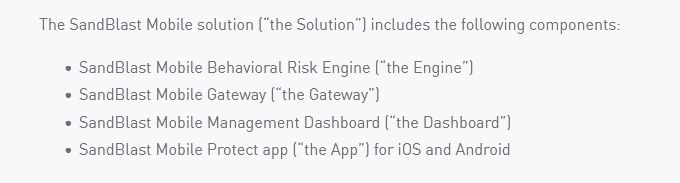
What are the different command sources that allow you to communicate with the API server?
Correct Answer:
B
🗳️
Reference:
https://sc1.checkpoint.com/documents/R80/APIs/#introduction%20
What makes Anti-Bot unique compared to other Threat Prevention mechanisms, such as URL Filtering, Anti-Virus, IPS, and Threat Emulation?
Correct Answer:
D
🗳️
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_AntiBotAntiVirus_AdminGuide/index.html
Which TCP-port does CPM process listen to?
Correct Answer:
D
🗳️
Reference:
https://www.checkpoint.com/downloads/products/r80.10-security-management-architecture-overview.pdf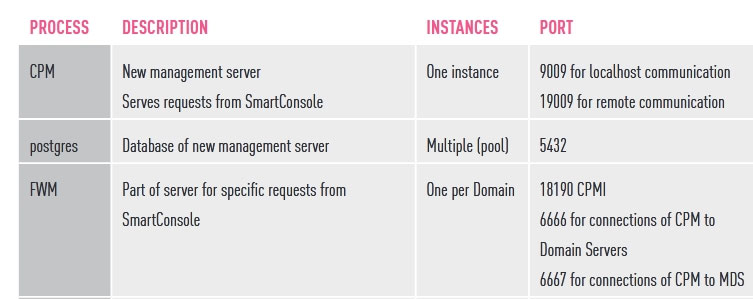
Which method below is NOT one of the ways to communicate using the Management API's?
Correct Answer:
D
🗳️
Reference:
https://sc1.checkpoint.com/documents/R80/APIs/#introduction%20
Your manager asked you to check the status of SecureXL, and its enabled templates and features. What command will you use to provide such information to manager?
Correct Answer:
B
🗳️
Reference:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk41397
SSL Network Extender (SNX) is a thin SSL VPN on-demand client that is installed on the remote user's machine via the web browser. What are the two modes of
SNX?
Correct Answer:
B
🗳️
Reference:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk67820
Which command would disable a Cluster Member permanently?
Correct Answer:
C
🗳️
Which two of these Check Point Protocols are used by SmartEvent Processes?
Correct Answer:
D
🗳️