

A new browser version has been deployed to all users at a company. After the deployment, users report that they can no longer access the company's secure time-card system, which is hosted by a SaaS provider. A technician investigates and discovers a security error is received upon opening the site. If the browser is rolled back to the older version, the site is accessible again. Which of the following is the MOST likely cause of the security error users are seeing?
Correct Answer:
C
🗳️
SIMULATION -
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday. The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations. The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
Review the network architecture and supporting documents and fulfill these requirements:
Part 1:
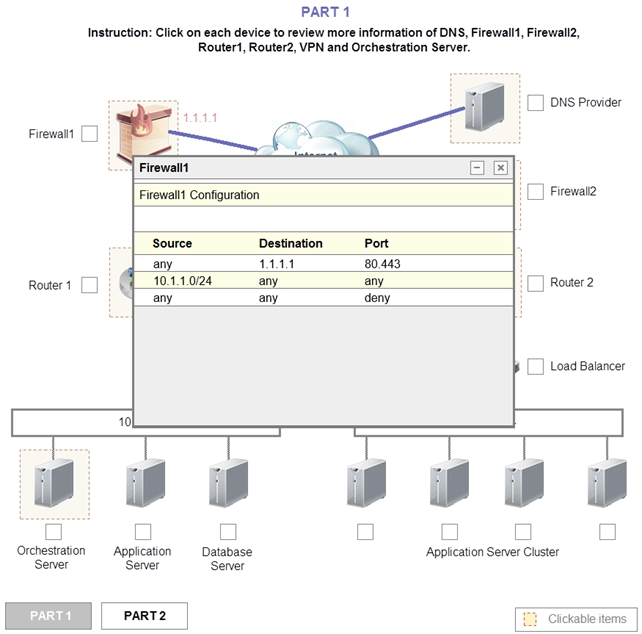
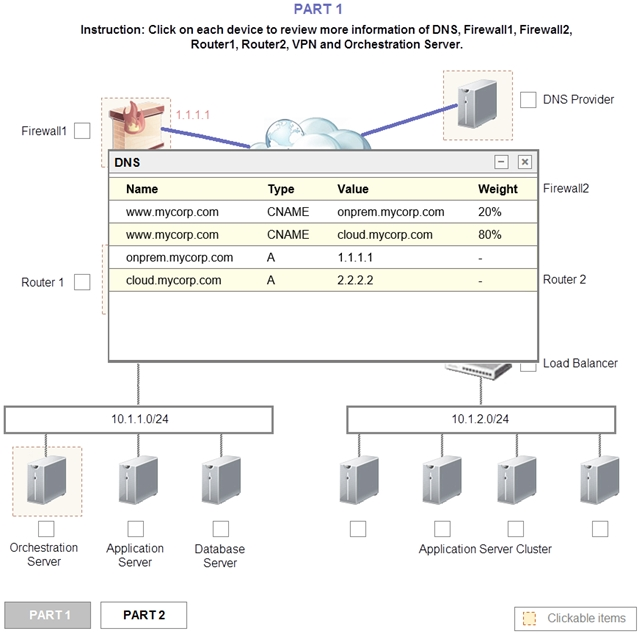
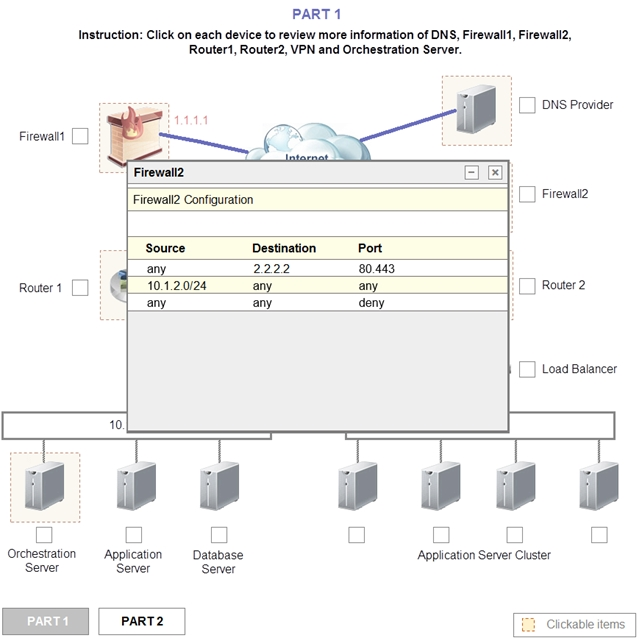
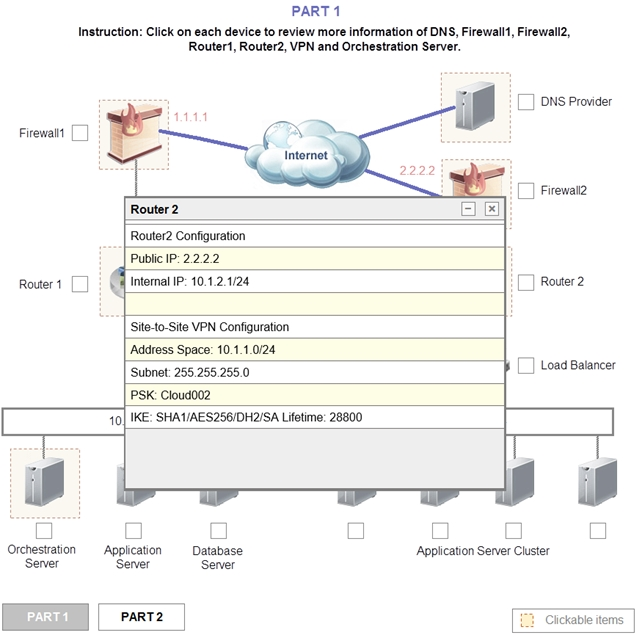
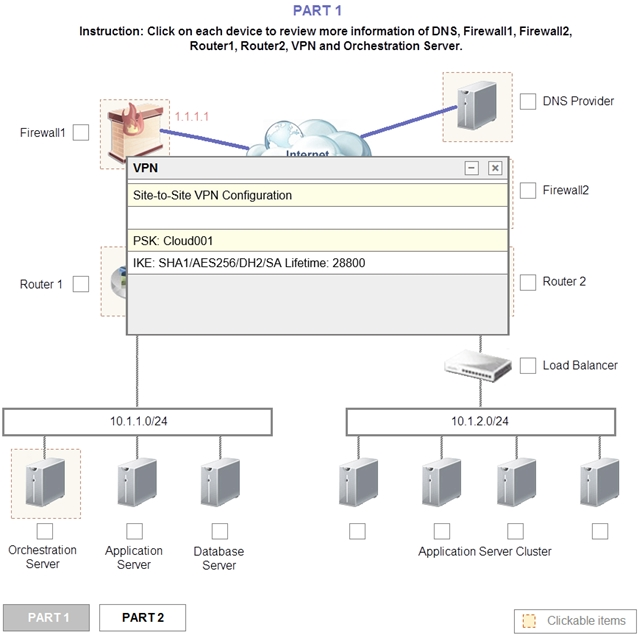
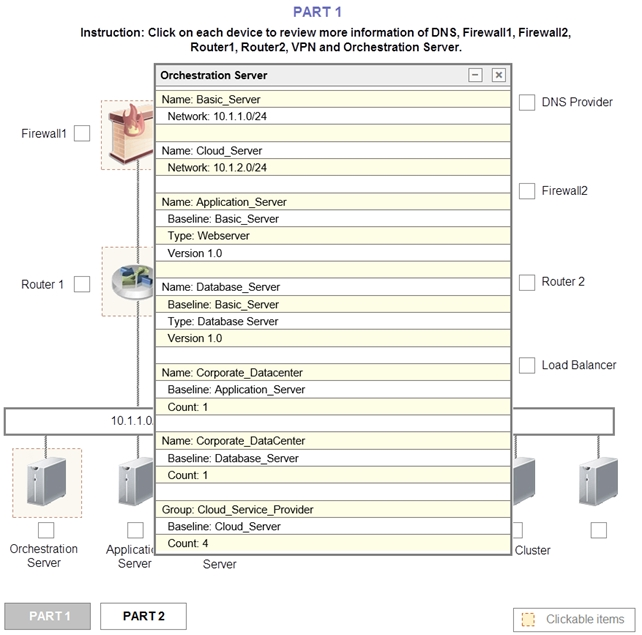
1. Analyze the configuration of the following components: DNS, Firewall1, Firewall2, Router1, Rouler2, VPN and Orchestrator Server.
2. Identify the problematic device(s).
Part 2:
3. Identify the correct options to provide adequate configuration for hybrid cloud architecture.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Simulation -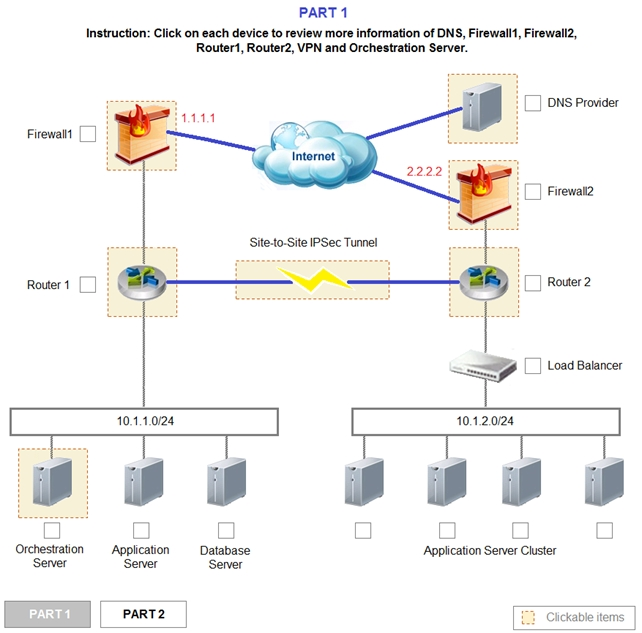
Correct Answer:
See the solution below.
Part 1:
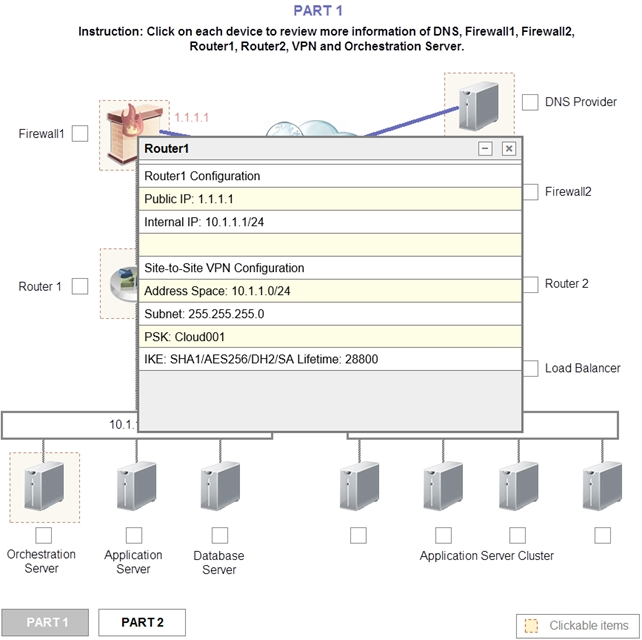
Router 2 is the problem and this should be selected. If you examine the preshared key used for the VPN you will see that it is not configured with the correct key.
It is using Cloud002 while router1 is using Cloud001
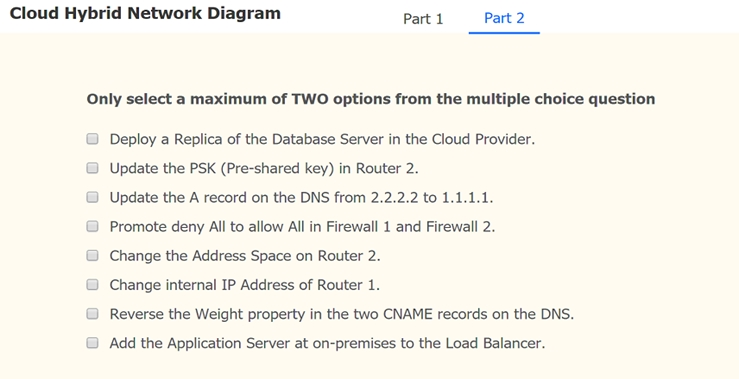
Part 2:
Update the PSK (Pre-shared key in Router2)
Add the Application Server at on-premises to the Load Balancer
DRAG DROP -
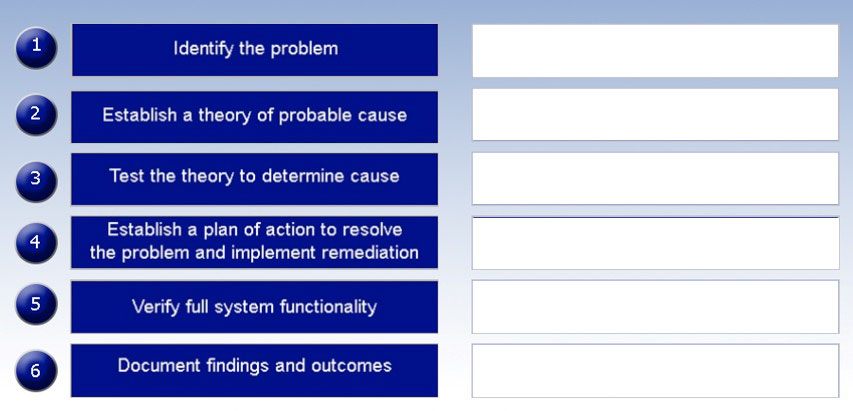
A hosted file share was infected with CryptoLocker and now root cause analysis needs to be performed. Place the tasks in the correct order according to the troubleshooting methodology.
Select and Place: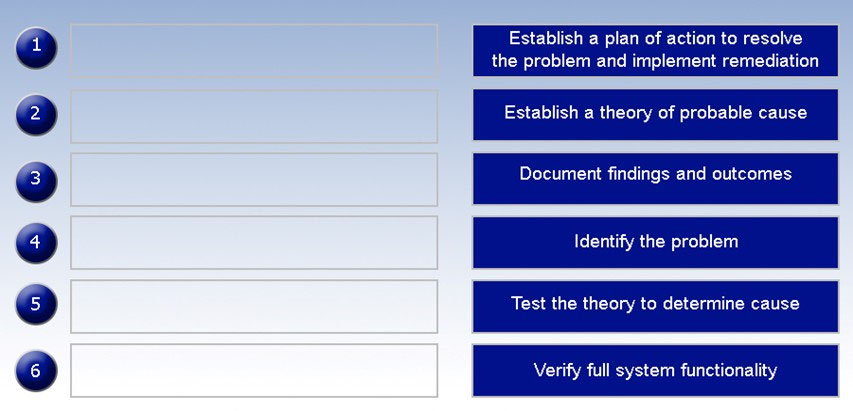
Correct Answer:
A company is seeking a new backup solution for its virtualized file servers that fits the following characteristics:
✑ The files stored on the servers are extremely large.
✑ Existing files receive multiple small changes per day.
✑ New files are only created once per month.
✑ All backups are being sent to a cloud repository.
Which of the following would BEST minimize backup size?
Correct Answer:
D
🗳️
A company has deployed a four-node cluster in a COLO environment with server configurations listed below. The company wants to ensure there is 50% overhead for failover and redundancy. There are currently eight VMs running within the cluster with four vCPUs x32GB each. The company wants to better utilize its resources within the cluster without compromising failover and redundancy.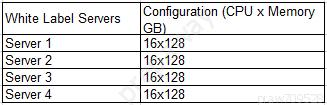
Given the information above, which of the following should a cloud administrator do to BEST accommodate failover and redundancy requirements?
Correct Answer:
B
🗳️
A courier company has virtualized its packing software application. The CSA needs to confirm the deployment is utilizing the correct amount of CPU per virtual instance. After confirming the deployment requirements, the CSA should log into the cloud services portal to ensure that:
Correct Answer:
C
🗳️
Due to a competitor's unlimited data plan, a service provider is struggling and wants to transform its business services to be more hosting oriented. A cloud architect is tasked to review current cloud resource capacity and provide recommendations and a plan for better resource utilization. Given the following report: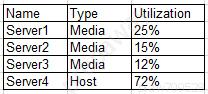
Which of the following is the BEST option for the architect to suggest?
Correct Answer:
A
🗳️
A cloud administrator is receiving alerts that the disk on several systems is 90% full. Upon reviewing the systems, the administrator determines that the log directory is using 50% of the disk. The company has a 14-day retention policy for all logs. Which of the following is the BEST solution to implement to minimize future alerts?
Correct Answer:
A
🗳️
A company purchased a SaaS CRM application. The signed SLA meets year-round performance requirements. Three months after deployment, customers start reporting a slow application response time. System availability, connectivity, and proper functionality still meet the SLA. Which of the following is MOST likely the reason for the poor response time?
Correct Answer:
C
🗳️
A cloud architect created a new delivery controller for a large VM farm to scale up according to organizational needs. The old and new delivery controllers now form a cluster. However, the new delivery controller returns an error when entering the license code. Which of the following is the MOST likely cause?
Correct Answer:
C
🗳️
Can't be a firewall issue, or the old delivery controller would have a license error as well. Based on the information given, I would say they are not licensed for clustering.